NEWS
js-controller 4.0.x jetzt für alle User im STABLE!
js-controller 4.0.x jetzt für alle User im STABLE!
-
@apollon77
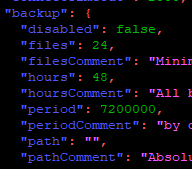
Seit js-controller Version 4.0.15 startet iobroker nach einem Restart nicht mehr, weil in der Datei "/opt/iobroker/iobroker-data/iobroker.json" der period Wert zu groß ist. Auch das heutige Update auf 4.0.18 bringt keine Änderung.In den Controller-Einstellungen sind 120 Minuten hinterlegt in der JSON Datei werden aber die Sekunden gespeichert, siehe Screenshot. Ändere ich die 7200000 in 120, startet iobroker wieder.
@blackeagle998 Jupp, bekannt und mit 4.0.18, welches gerade im Beta ist behoben. Ich habe keine Ahnung wo da bei dir so ein großer Wert überhaupt reingekommen ist
 Der war schon immer "Minuten" und nicht Sekunden oder Millisekunden
Der war schon immer "Minuten" und nicht Sekunden oder Millisekunden  Aber am Ende egal weil der "backup" Part leider bei controller <4 ignoriert wurde
Aber am Ende egal weil der "backup" Part leider bei controller <4 ignoriert wurde 
-
@blackeagle998 Jupp, bekannt und mit 4.0.18, welches gerade im Beta ist behoben. Ich habe keine Ahnung wo da bei dir so ein großer Wert überhaupt reingekommen ist
 Der war schon immer "Minuten" und nicht Sekunden oder Millisekunden
Der war schon immer "Minuten" und nicht Sekunden oder Millisekunden  Aber am Ende egal weil der "backup" Part leider bei controller <4 ignoriert wurde
Aber am Ende egal weil der "backup" Part leider bei controller <4 ignoriert wurde 
@apollon77
Meinst du eine andere 4.0.18 als ich installiert habe?
Mit der Version ist das jedenfalls gerade wieder passiert. -
@apollon77
Meinst du eine andere 4.0.18 als ich installiert habe?

Mit der Version ist das jedenfalls gerade wieder passiert.@blackeagle998 Was genau ist passiert? Also die 4.0.15 hatte den Bug das er gar nicht gestartet ist wenn der Wert zur gross war weil an der Code-Stelle wo eine Log Meldung ausgegeben werden sollte das der Wert falsch ist und runterkorrigiert wurde war ein Fehler.
Aber um nicht alle zu verwirren sollten wir Diskussionen zur BETA Version 4.0.18 bitte im beta Thread führen

-
Habe gerade 4.0.18 durchgeführt.
Alles geklappt, läuft einwandfrei. -
Heute kommt auch das js.controller update 4.0.18 ins Stable mit einigen kleineren Bugfixes die noch aufgefallen waren.
@apollon77 vielen Dank Installation 4.0.18 hat einwandfrei geklappt.


-
Heute kommt auch das js.controller update 4.0.18 ins Stable mit einigen kleineren Bugfixes die noch aufgefallen waren.
Die Installation 4.0.18 wurde mir heute angeboten und hat soweit auch problemlos geklappt.
Alles läuft!
Habe jedoch diese Meldungen beim Update bekommen:The following notifications happened during sync: - Ignoring Directory "info.admin" because officially not created as meta object. Please remove directory! - Ignoring Directory "netatmo-energy.admin" because officially not created as meta object. Please remove directory!Was bedeutet das?
Kann oder muss ich da was tun? -
Die Installation 4.0.18 wurde mir heute angeboten und hat soweit auch problemlos geklappt.
Alles läuft!
Habe jedoch diese Meldungen beim Update bekommen:The following notifications happened during sync: - Ignoring Directory "info.admin" because officially not created as meta object. Please remove directory! - Ignoring Directory "netatmo-energy.admin" because officially not created as meta object. Please remove directory!Was bedeutet das?
Kann oder muss ich da was tun?@pupsimupsi sagte in js-controller 4.0.x jetzt für alle User im STABLE!:
Was bedeutet das?
Kann oder muss ich da was tun?Steht oben in der FAQ ... Post #2 in diesem Thread

-
@pupsimupsi sagte in js-controller 4.0.x jetzt für alle User im STABLE!:
Was bedeutet das?
Kann oder muss ich da was tun?Steht oben in der FAQ ... Post #2 in diesem Thread

DANKE und sorry!
Habe nach dem erfolgreichen Update auf Version 4 nicht damit gerechnet das nach einem weiteren Update auf eine höhere 4er Version die gleichen Fehler passieren können...Habe gerade "iob upload all" durchgeführt.
War´s das?
Kann ich das iwie prüfen ob nun alles OK ist? -
DANKE und sorry!
Habe nach dem erfolgreichen Update auf Version 4 nicht damit gerechnet das nach einem weiteren Update auf eine höhere 4er Version die gleichen Fehler passieren können...Habe gerade "iob upload all" durchgeführt.
War´s das?
Kann ich das iwie prüfen ob nun alles OK ist?@pupsimupsi Jett liess nochmal oben ... da steht was Du tun kannst wenn diese meldungen kommen. Da sind Daten "out of sync" oder wurden ggf nicht aufgeräumt irgendwann mal. Da steht nicht das irgendein Automatismus dies gefixt hat.
Und für dich mal herkopiert was oben steht:
Bitte ein iob upload all ausführen. Falls Einträge von Adaptern enthalten sein sollten die nicht mehr installiert sind, dann können diese Dateien manuell gelöscht werden.
Aaaaalllssoooooo ... sind denn info und netatmo-energy bei Dir noch installiert?
-
@pupsimupsi Jett liess nochmal oben ... da steht was Du tun kannst wenn diese meldungen kommen. Da sind Daten "out of sync" oder wurden ggf nicht aufgeräumt irgendwann mal. Da steht nicht das irgendein Automatismus dies gefixt hat.
Und für dich mal herkopiert was oben steht:
Bitte ein iob upload all ausführen. Falls Einträge von Adaptern enthalten sein sollten die nicht mehr installiert sind, dann können diese Dateien manuell gelöscht werden.
Aaaaalllssoooooo ... sind denn info und netatmo-energy bei Dir noch installiert?
Aaaaalllssoooooo:
Da muss wohl etwas falsch rüber gekommen sein...!?
Ich habe, wie gesagt, nach deinem Hinweis, die FAQ gelesen und "iob upload all" ausgeführt.Von nem automatischem Fix o.Ä., hab ich nie gesprochen...

Ich wollte lediglich wissen, ob ich evtl. irgendwie überprüfen kann, dass nun (nach dem iob upload all) alles "OK" ist.
Sorry für´s Nachfragen. Das verkneif ich mir in Zukunft...
Ja, sind beide noch installiert.
Netatmo-energy sogar recht frisch. Erst seit ein paar Tagen. -
Aaaaalllssoooooo:
Da muss wohl etwas falsch rüber gekommen sein...!?
Ich habe, wie gesagt, nach deinem Hinweis, die FAQ gelesen und "iob upload all" ausgeführt.Von nem automatischem Fix o.Ä., hab ich nie gesprochen...

Ich wollte lediglich wissen, ob ich evtl. irgendwie überprüfen kann, dass nun (nach dem iob upload all) alles "OK" ist.
Sorry für´s Nachfragen. Das verkneif ich mir in Zukunft...
Ja, sind beide noch installiert.
Netatmo-energy sogar recht frisch. Erst seit ein paar Tagen.Hallo zusammen,
bekomme beim Versich von 4.0.15 auf 4.0.18 upzudaten folgenden Fehler:
host.ioBroker Cannot install iobroker.js-controller@4.0.18: 217Ich bin nach Anleitung vorgegangen, also iob stop, iob update, iob fix und dann iob upgrade self.
-
Hallo zusammen,
bekomme beim Versich von 4.0.15 auf 4.0.18 upzudaten folgenden Fehler:
host.ioBroker Cannot install iobroker.js-controller@4.0.18: 217Ich bin nach Anleitung vorgegangen, also iob stop, iob update, iob fix und dann iob upgrade self.
@feinfinger da wird was mit npm sein
machmal
npm i iobroker.js-controller@4.0.18 --productiondann siehst du wo es hängt
-
Aaaaalllssoooooo:
Da muss wohl etwas falsch rüber gekommen sein...!?
Ich habe, wie gesagt, nach deinem Hinweis, die FAQ gelesen und "iob upload all" ausgeführt.Von nem automatischem Fix o.Ä., hab ich nie gesprochen...

Ich wollte lediglich wissen, ob ich evtl. irgendwie überprüfen kann, dass nun (nach dem iob upload all) alles "OK" ist.
Sorry für´s Nachfragen. Das verkneif ich mir in Zukunft...
Ja, sind beide noch installiert.
Netatmo-energy sogar recht frisch. Erst seit ein paar Tagen.@pupsimupsi sagte in js-controller 4.0.x jetzt für alle User im STABLE!:
Sorry für´s Nachfragen. Das verkneif ich mir in Zukunft...
Alles gut, nachfragen darf man immer. Wenn nur Infos fehlen was Du gemacht hast kann ich nur bestmöglich raten ... Und dann kommen manchmal solche Antworten bei raus.
Ja, sind beide noch installiert.
Netatmo-energy sogar recht frisch. Erst seit ein paar Tagen.Dann sollte das "upload all" das Problem gefixt haben ... wirst DU beim nächsten js-controller update sehen

-
@feinfinger da wird was mit npm sein
machmal
npm i iobroker.js-controller@4.0.18 --productiondann siehst du wo es hängt
root@ioBroker:~# npm i iobroker.js-controller@4.0.18 --production added 150 packages, removed 169 packages, changed 46 packages, and audited 311 packages in 1m 16 packages are looking for funding run `npm fund` for details 4 moderate severity vulnerabilities To address all issues (including breaking changes), run: npm audit fix --force Run `npm audit` for details. root@ioBroker:~# npm fund root +-- https://opencollective.com/ioredis | `-- ioredis@4.28.5 +-- https://github.com/sindresorhus/execa?sponsor=1 | | `-- execa@5.1.1 | `-- https://github.com/sponsors/sindresorhus | `-- get-stream@6.0.1, is-stream@2.0.1, onetime@5.1.2 +-- https://github.com/sponsors/RubenVerborgh | `-- follow-redirects@1.14.9 +-- https://paulmillr.com/funding/ | | `-- chokidar@3.5.3 | `-- https://github.com/sponsors/jonschlinkert | `-- picomatch@2.3.1 +-- https://github.com/sponsors/feross | `-- safe-buffer@5.2.1 +-- https://github.com/sponsors/ljharb | `-- is-nan@1.3.2, call-bind@1.0.2, get-intrinsic@1.1.1, has-symbols@1.0.3 +-- https://github.com/sponsors/epoberezkin | `-- ajv@6.12.6 `-- https://github.com/chalk/wrap-ansi?sponsor=1 | `-- wrap-ansi@7.0.0 `-- https://github.com/chalk/ansi-styles?sponsor=1 `-- ansi-styles@4.3.0 root@ioBroker:~# npm audit # npm audit report ansi-regex >2.1.1 <5.0.1 Severity: moderate Inefficient Regular Expression Complexity in chalk/ansi-regex - https://github.com/advisories/GHSA-93q8-gq69-wqmw fix available via `npm audit fix` node_modules/ansi-regex strip-ansi 4.0.0 - 5.2.0 Depends on vulnerable versions of ansi-regex node_modules/strip-ansi cliui 4.0.0 - 5.0.0 Depends on vulnerable versions of strip-ansi node_modules/cliui yargs 8.0.0-candidate.0 - 15.0.0 Depends on vulnerable versions of cliui Depends on vulnerable versions of yargs-parser node_modules/yargs iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller string-width 2.1.0 - 4.1.0 Depends on vulnerable versions of strip-ansi node_modules/string-width debug <2.6.9 Regular Expression Denial of Service in debug - https://github.com/advisories/GHSA-gxpj-cx7g-858c fix available via `npm audit fix` node_modules/engine.io-client/node_modules/debug node_modules/engine.io/node_modules/debug node_modules/socket.io-adapter/node_modules/debug node_modules/socket.io-client/node_modules/debug node_modules/socket.io-parser/node_modules/debug node_modules/socket.io/node_modules/debug engine.io <=4.0.0-alpha.1 Depends on vulnerable versions of debug Depends on vulnerable versions of ws node_modules/engine.io socket.io <=2.4.1 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io Depends on vulnerable versions of socket.io-parser node_modules/socket.io iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller engine.io-client <=3.3.2 || 3.4.0 - 3.5.1 || 4.0.0-alpha.0 - 4.1.3 Depends on vulnerable versions of debug Depends on vulnerable versions of parsejson Depends on vulnerable versions of ws Depends on vulnerable versions of xmlhttprequest-ssl node_modules/engine.io-client socket.io-client 1.0.0-pre - 2.1.1 || 2.3.0 - 2.3.1 || 3.0.0-rc1 - 3.0.5 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io-client Depends on vulnerable versions of socket.io-parser node_modules/socket.io-client socket.io-adapter <=1.1.0 Depends on vulnerable versions of debug Depends on vulnerable versions of socket.io-parser node_modules/socket.io-adapter socket.io-parser <=3.3.1 Depends on vulnerable versions of debug node_modules/socket.io-parser engine.io <=4.0.0-alpha.1 Severity: high Resource exhaustion in engine.io - https://github.com/advisories/GHSA-j4f2-536g-r55m Depends on vulnerable versions of debug Depends on vulnerable versions of ws fix available via `npm audit fix` node_modules/engine.io socket.io <=2.4.1 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io Depends on vulnerable versions of socket.io-parser node_modules/socket.io iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller iobroker.js-controller <=2.1.1 Severity: high Arbitrary File Write in iobroker.js-controller - https://github.com/advisories/GHSA-cmch-296j-wfvw Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs fix available via `npm audit fix` node_modules/iobroker.js-controller minimist <0.2.1 Severity: moderate Prototype Pollution in minimist - https://github.com/advisories/GHSA-vh95-rmgr-6w4m fix available via `npm audit fix` node_modules/winston-daily-rotate-file/node_modules/minimist mkdirp 0.4.1 - 0.5.1 Depends on vulnerable versions of minimist node_modules/winston-daily-rotate-file/node_modules/mkdirp winston-daily-rotate-file 1.7.0 - 1.7.2 Depends on vulnerable versions of mkdirp node_modules/winston-daily-rotate-file iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller parsejson * Severity: high Regular Expression Denial of Service in parsejson - https://github.com/advisories/GHSA-q75g-2496-mxpp fix available via `npm audit fix` node_modules/parsejson engine.io-client <=3.3.2 || 3.4.0 - 3.5.1 || 4.0.0-alpha.0 - 4.1.3 Depends on vulnerable versions of debug Depends on vulnerable versions of parsejson Depends on vulnerable versions of ws Depends on vulnerable versions of xmlhttprequest-ssl node_modules/engine.io-client socket.io-client 1.0.0-pre - 2.1.1 || 2.3.0 - 2.3.1 || 3.0.0-rc1 - 3.0.5 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io-client Depends on vulnerable versions of socket.io-parser node_modules/socket.io-client iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller redis 2.6.0 - 3.1.0 Potential exponential regex in monitor mode - https://github.com/advisories/GHSA-35q2-47q7-3pc3 fix available via `npm audit fix` node_modules/redis iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller socket.io <=2.4.1 Severity: high Insecure defaults due to CORS misconfiguration in socket.io - https://github.com/advisories/GHSA-fxwf-4rqh-v8g3 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io Depends on vulnerable versions of socket.io-parser fix available via `npm audit fix` node_modules/socket.io iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller socket.io-parser <=3.3.1 Severity: high Resource exhaustion in socket.io-parser - https://github.com/advisories/GHSA-xfhh-g9f5-x4m4 Depends on vulnerable versions of debug fix available via `npm audit fix` node_modules/socket.io-parser socket.io <=2.4.1 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io Depends on vulnerable versions of socket.io-parser node_modules/socket.io iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller socket.io-adapter <=1.1.0 Depends on vulnerable versions of debug Depends on vulnerable versions of socket.io-parser node_modules/socket.io-adapter socket.io-client 1.0.0-pre - 2.1.1 || 2.3.0 - 2.3.1 || 3.0.0-rc1 - 3.0.5 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io-client Depends on vulnerable versions of socket.io-parser node_modules/socket.io-client ws <=1.1.4 Severity: high Denial of Service in ws - https://github.com/advisories/GHSA-5v72-xg48-5rpm fix available via `npm audit fix` node_modules/engine.io-client/node_modules/ws node_modules/engine.io/node_modules/ws engine.io <=4.0.0-alpha.1 Depends on vulnerable versions of debug Depends on vulnerable versions of ws node_modules/engine.io socket.io <=2.4.1 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io Depends on vulnerable versions of socket.io-parser node_modules/socket.io iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller engine.io-client <=3.3.2 || 3.4.0 - 3.5.1 || 4.0.0-alpha.0 - 4.1.3 Depends on vulnerable versions of debug Depends on vulnerable versions of parsejson Depends on vulnerable versions of ws Depends on vulnerable versions of xmlhttprequest-ssl node_modules/engine.io-client socket.io-client 1.0.0-pre - 2.1.1 || 2.3.0 - 2.3.1 || 3.0.0-rc1 - 3.0.5 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io-client Depends on vulnerable versions of socket.io-parser node_modules/socket.io-client xmlhttprequest-ssl <=1.6.1 Severity: critical Improper Certificate Validation in xmlhttprequest-ssl - https://github.com/advisories/GHSA-72mh-269x-7mh5 Arbitrary Code Injection - https://github.com/advisories/GHSA-h4j5-c7cj-74xg fix available via `npm audit fix` node_modules/xmlhttprequest-ssl engine.io-client <=3.3.2 || 3.4.0 - 3.5.1 || 4.0.0-alpha.0 - 4.1.3 Depends on vulnerable versions of debug Depends on vulnerable versions of parsejson Depends on vulnerable versions of ws Depends on vulnerable versions of xmlhttprequest-ssl node_modules/engine.io-client socket.io-client 1.0.0-pre - 2.1.1 || 2.3.0 - 2.3.1 || 3.0.0-rc1 - 3.0.5 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io-client Depends on vulnerable versions of socket.io-parser node_modules/socket.io-client iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller yargs-parser 6.0.0 - 13.1.1 Severity: moderate Prototype Pollution in yargs-parser - https://github.com/advisories/GHSA-p9pc-299p-vxgp fix available via `npm audit fix` node_modules/yargs-parser yargs 8.0.0-candidate.0 - 15.0.0 Depends on vulnerable versions of cliui Depends on vulnerable versions of yargs-parser node_modules/yargs iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller 21 vulnerabilities (2 low, 9 moderate, 7 high, 3 critical) To address all issues, run: npm audit fixbedeutet das ein npm audit fix ausführen?
-
root@ioBroker:~# npm i iobroker.js-controller@4.0.18 --production added 150 packages, removed 169 packages, changed 46 packages, and audited 311 packages in 1m 16 packages are looking for funding run `npm fund` for details 4 moderate severity vulnerabilities To address all issues (including breaking changes), run: npm audit fix --force Run `npm audit` for details. root@ioBroker:~# npm fund root +-- https://opencollective.com/ioredis | `-- ioredis@4.28.5 +-- https://github.com/sindresorhus/execa?sponsor=1 | | `-- execa@5.1.1 | `-- https://github.com/sponsors/sindresorhus | `-- get-stream@6.0.1, is-stream@2.0.1, onetime@5.1.2 +-- https://github.com/sponsors/RubenVerborgh | `-- follow-redirects@1.14.9 +-- https://paulmillr.com/funding/ | | `-- chokidar@3.5.3 | `-- https://github.com/sponsors/jonschlinkert | `-- picomatch@2.3.1 +-- https://github.com/sponsors/feross | `-- safe-buffer@5.2.1 +-- https://github.com/sponsors/ljharb | `-- is-nan@1.3.2, call-bind@1.0.2, get-intrinsic@1.1.1, has-symbols@1.0.3 +-- https://github.com/sponsors/epoberezkin | `-- ajv@6.12.6 `-- https://github.com/chalk/wrap-ansi?sponsor=1 | `-- wrap-ansi@7.0.0 `-- https://github.com/chalk/ansi-styles?sponsor=1 `-- ansi-styles@4.3.0 root@ioBroker:~# npm audit # npm audit report ansi-regex >2.1.1 <5.0.1 Severity: moderate Inefficient Regular Expression Complexity in chalk/ansi-regex - https://github.com/advisories/GHSA-93q8-gq69-wqmw fix available via `npm audit fix` node_modules/ansi-regex strip-ansi 4.0.0 - 5.2.0 Depends on vulnerable versions of ansi-regex node_modules/strip-ansi cliui 4.0.0 - 5.0.0 Depends on vulnerable versions of strip-ansi node_modules/cliui yargs 8.0.0-candidate.0 - 15.0.0 Depends on vulnerable versions of cliui Depends on vulnerable versions of yargs-parser node_modules/yargs iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller string-width 2.1.0 - 4.1.0 Depends on vulnerable versions of strip-ansi node_modules/string-width debug <2.6.9 Regular Expression Denial of Service in debug - https://github.com/advisories/GHSA-gxpj-cx7g-858c fix available via `npm audit fix` node_modules/engine.io-client/node_modules/debug node_modules/engine.io/node_modules/debug node_modules/socket.io-adapter/node_modules/debug node_modules/socket.io-client/node_modules/debug node_modules/socket.io-parser/node_modules/debug node_modules/socket.io/node_modules/debug engine.io <=4.0.0-alpha.1 Depends on vulnerable versions of debug Depends on vulnerable versions of ws node_modules/engine.io socket.io <=2.4.1 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io Depends on vulnerable versions of socket.io-parser node_modules/socket.io iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller engine.io-client <=3.3.2 || 3.4.0 - 3.5.1 || 4.0.0-alpha.0 - 4.1.3 Depends on vulnerable versions of debug Depends on vulnerable versions of parsejson Depends on vulnerable versions of ws Depends on vulnerable versions of xmlhttprequest-ssl node_modules/engine.io-client socket.io-client 1.0.0-pre - 2.1.1 || 2.3.0 - 2.3.1 || 3.0.0-rc1 - 3.0.5 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io-client Depends on vulnerable versions of socket.io-parser node_modules/socket.io-client socket.io-adapter <=1.1.0 Depends on vulnerable versions of debug Depends on vulnerable versions of socket.io-parser node_modules/socket.io-adapter socket.io-parser <=3.3.1 Depends on vulnerable versions of debug node_modules/socket.io-parser engine.io <=4.0.0-alpha.1 Severity: high Resource exhaustion in engine.io - https://github.com/advisories/GHSA-j4f2-536g-r55m Depends on vulnerable versions of debug Depends on vulnerable versions of ws fix available via `npm audit fix` node_modules/engine.io socket.io <=2.4.1 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io Depends on vulnerable versions of socket.io-parser node_modules/socket.io iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller iobroker.js-controller <=2.1.1 Severity: high Arbitrary File Write in iobroker.js-controller - https://github.com/advisories/GHSA-cmch-296j-wfvw Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs fix available via `npm audit fix` node_modules/iobroker.js-controller minimist <0.2.1 Severity: moderate Prototype Pollution in minimist - https://github.com/advisories/GHSA-vh95-rmgr-6w4m fix available via `npm audit fix` node_modules/winston-daily-rotate-file/node_modules/minimist mkdirp 0.4.1 - 0.5.1 Depends on vulnerable versions of minimist node_modules/winston-daily-rotate-file/node_modules/mkdirp winston-daily-rotate-file 1.7.0 - 1.7.2 Depends on vulnerable versions of mkdirp node_modules/winston-daily-rotate-file iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller parsejson * Severity: high Regular Expression Denial of Service in parsejson - https://github.com/advisories/GHSA-q75g-2496-mxpp fix available via `npm audit fix` node_modules/parsejson engine.io-client <=3.3.2 || 3.4.0 - 3.5.1 || 4.0.0-alpha.0 - 4.1.3 Depends on vulnerable versions of debug Depends on vulnerable versions of parsejson Depends on vulnerable versions of ws Depends on vulnerable versions of xmlhttprequest-ssl node_modules/engine.io-client socket.io-client 1.0.0-pre - 2.1.1 || 2.3.0 - 2.3.1 || 3.0.0-rc1 - 3.0.5 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io-client Depends on vulnerable versions of socket.io-parser node_modules/socket.io-client iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller redis 2.6.0 - 3.1.0 Potential exponential regex in monitor mode - https://github.com/advisories/GHSA-35q2-47q7-3pc3 fix available via `npm audit fix` node_modules/redis iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller socket.io <=2.4.1 Severity: high Insecure defaults due to CORS misconfiguration in socket.io - https://github.com/advisories/GHSA-fxwf-4rqh-v8g3 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io Depends on vulnerable versions of socket.io-parser fix available via `npm audit fix` node_modules/socket.io iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller socket.io-parser <=3.3.1 Severity: high Resource exhaustion in socket.io-parser - https://github.com/advisories/GHSA-xfhh-g9f5-x4m4 Depends on vulnerable versions of debug fix available via `npm audit fix` node_modules/socket.io-parser socket.io <=2.4.1 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io Depends on vulnerable versions of socket.io-parser node_modules/socket.io iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller socket.io-adapter <=1.1.0 Depends on vulnerable versions of debug Depends on vulnerable versions of socket.io-parser node_modules/socket.io-adapter socket.io-client 1.0.0-pre - 2.1.1 || 2.3.0 - 2.3.1 || 3.0.0-rc1 - 3.0.5 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io-client Depends on vulnerable versions of socket.io-parser node_modules/socket.io-client ws <=1.1.4 Severity: high Denial of Service in ws - https://github.com/advisories/GHSA-5v72-xg48-5rpm fix available via `npm audit fix` node_modules/engine.io-client/node_modules/ws node_modules/engine.io/node_modules/ws engine.io <=4.0.0-alpha.1 Depends on vulnerable versions of debug Depends on vulnerable versions of ws node_modules/engine.io socket.io <=2.4.1 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io Depends on vulnerable versions of socket.io-parser node_modules/socket.io iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller engine.io-client <=3.3.2 || 3.4.0 - 3.5.1 || 4.0.0-alpha.0 - 4.1.3 Depends on vulnerable versions of debug Depends on vulnerable versions of parsejson Depends on vulnerable versions of ws Depends on vulnerable versions of xmlhttprequest-ssl node_modules/engine.io-client socket.io-client 1.0.0-pre - 2.1.1 || 2.3.0 - 2.3.1 || 3.0.0-rc1 - 3.0.5 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io-client Depends on vulnerable versions of socket.io-parser node_modules/socket.io-client xmlhttprequest-ssl <=1.6.1 Severity: critical Improper Certificate Validation in xmlhttprequest-ssl - https://github.com/advisories/GHSA-72mh-269x-7mh5 Arbitrary Code Injection - https://github.com/advisories/GHSA-h4j5-c7cj-74xg fix available via `npm audit fix` node_modules/xmlhttprequest-ssl engine.io-client <=3.3.2 || 3.4.0 - 3.5.1 || 4.0.0-alpha.0 - 4.1.3 Depends on vulnerable versions of debug Depends on vulnerable versions of parsejson Depends on vulnerable versions of ws Depends on vulnerable versions of xmlhttprequest-ssl node_modules/engine.io-client socket.io-client 1.0.0-pre - 2.1.1 || 2.3.0 - 2.3.1 || 3.0.0-rc1 - 3.0.5 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io-client Depends on vulnerable versions of socket.io-parser node_modules/socket.io-client iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller yargs-parser 6.0.0 - 13.1.1 Severity: moderate Prototype Pollution in yargs-parser - https://github.com/advisories/GHSA-p9pc-299p-vxgp fix available via `npm audit fix` node_modules/yargs-parser yargs 8.0.0-candidate.0 - 15.0.0 Depends on vulnerable versions of cliui Depends on vulnerable versions of yargs-parser node_modules/yargs iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller 21 vulnerabilities (2 low, 9 moderate, 7 high, 3 critical) To address all issues, run: npm audit fixbedeutet das ein npm audit fix ausführen?
@feinfinger sagte in js-controller 4.0.x jetzt für alle User im STABLE!:
bedeutet das ein npm audit fix ausführen?
NEIN..
und stell dich mal richtig hin
cd /opt/iobroker npm i iobroker.js-controller@4.0.18 --productionund erst dann
wobei mach direkt die .19 drauf
npm i iobroker.js-controller@4.0.19 --production -
root@ioBroker:~# npm i iobroker.js-controller@4.0.18 --production added 150 packages, removed 169 packages, changed 46 packages, and audited 311 packages in 1m 16 packages are looking for funding run `npm fund` for details 4 moderate severity vulnerabilities To address all issues (including breaking changes), run: npm audit fix --force Run `npm audit` for details. root@ioBroker:~# npm fund root +-- https://opencollective.com/ioredis | `-- ioredis@4.28.5 +-- https://github.com/sindresorhus/execa?sponsor=1 | | `-- execa@5.1.1 | `-- https://github.com/sponsors/sindresorhus | `-- get-stream@6.0.1, is-stream@2.0.1, onetime@5.1.2 +-- https://github.com/sponsors/RubenVerborgh | `-- follow-redirects@1.14.9 +-- https://paulmillr.com/funding/ | | `-- chokidar@3.5.3 | `-- https://github.com/sponsors/jonschlinkert | `-- picomatch@2.3.1 +-- https://github.com/sponsors/feross | `-- safe-buffer@5.2.1 +-- https://github.com/sponsors/ljharb | `-- is-nan@1.3.2, call-bind@1.0.2, get-intrinsic@1.1.1, has-symbols@1.0.3 +-- https://github.com/sponsors/epoberezkin | `-- ajv@6.12.6 `-- https://github.com/chalk/wrap-ansi?sponsor=1 | `-- wrap-ansi@7.0.0 `-- https://github.com/chalk/ansi-styles?sponsor=1 `-- ansi-styles@4.3.0 root@ioBroker:~# npm audit # npm audit report ansi-regex >2.1.1 <5.0.1 Severity: moderate Inefficient Regular Expression Complexity in chalk/ansi-regex - https://github.com/advisories/GHSA-93q8-gq69-wqmw fix available via `npm audit fix` node_modules/ansi-regex strip-ansi 4.0.0 - 5.2.0 Depends on vulnerable versions of ansi-regex node_modules/strip-ansi cliui 4.0.0 - 5.0.0 Depends on vulnerable versions of strip-ansi node_modules/cliui yargs 8.0.0-candidate.0 - 15.0.0 Depends on vulnerable versions of cliui Depends on vulnerable versions of yargs-parser node_modules/yargs iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller string-width 2.1.0 - 4.1.0 Depends on vulnerable versions of strip-ansi node_modules/string-width debug <2.6.9 Regular Expression Denial of Service in debug - https://github.com/advisories/GHSA-gxpj-cx7g-858c fix available via `npm audit fix` node_modules/engine.io-client/node_modules/debug node_modules/engine.io/node_modules/debug node_modules/socket.io-adapter/node_modules/debug node_modules/socket.io-client/node_modules/debug node_modules/socket.io-parser/node_modules/debug node_modules/socket.io/node_modules/debug engine.io <=4.0.0-alpha.1 Depends on vulnerable versions of debug Depends on vulnerable versions of ws node_modules/engine.io socket.io <=2.4.1 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io Depends on vulnerable versions of socket.io-parser node_modules/socket.io iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller engine.io-client <=3.3.2 || 3.4.0 - 3.5.1 || 4.0.0-alpha.0 - 4.1.3 Depends on vulnerable versions of debug Depends on vulnerable versions of parsejson Depends on vulnerable versions of ws Depends on vulnerable versions of xmlhttprequest-ssl node_modules/engine.io-client socket.io-client 1.0.0-pre - 2.1.1 || 2.3.0 - 2.3.1 || 3.0.0-rc1 - 3.0.5 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io-client Depends on vulnerable versions of socket.io-parser node_modules/socket.io-client socket.io-adapter <=1.1.0 Depends on vulnerable versions of debug Depends on vulnerable versions of socket.io-parser node_modules/socket.io-adapter socket.io-parser <=3.3.1 Depends on vulnerable versions of debug node_modules/socket.io-parser engine.io <=4.0.0-alpha.1 Severity: high Resource exhaustion in engine.io - https://github.com/advisories/GHSA-j4f2-536g-r55m Depends on vulnerable versions of debug Depends on vulnerable versions of ws fix available via `npm audit fix` node_modules/engine.io socket.io <=2.4.1 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io Depends on vulnerable versions of socket.io-parser node_modules/socket.io iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller iobroker.js-controller <=2.1.1 Severity: high Arbitrary File Write in iobroker.js-controller - https://github.com/advisories/GHSA-cmch-296j-wfvw Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs fix available via `npm audit fix` node_modules/iobroker.js-controller minimist <0.2.1 Severity: moderate Prototype Pollution in minimist - https://github.com/advisories/GHSA-vh95-rmgr-6w4m fix available via `npm audit fix` node_modules/winston-daily-rotate-file/node_modules/minimist mkdirp 0.4.1 - 0.5.1 Depends on vulnerable versions of minimist node_modules/winston-daily-rotate-file/node_modules/mkdirp winston-daily-rotate-file 1.7.0 - 1.7.2 Depends on vulnerable versions of mkdirp node_modules/winston-daily-rotate-file iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller parsejson * Severity: high Regular Expression Denial of Service in parsejson - https://github.com/advisories/GHSA-q75g-2496-mxpp fix available via `npm audit fix` node_modules/parsejson engine.io-client <=3.3.2 || 3.4.0 - 3.5.1 || 4.0.0-alpha.0 - 4.1.3 Depends on vulnerable versions of debug Depends on vulnerable versions of parsejson Depends on vulnerable versions of ws Depends on vulnerable versions of xmlhttprequest-ssl node_modules/engine.io-client socket.io-client 1.0.0-pre - 2.1.1 || 2.3.0 - 2.3.1 || 3.0.0-rc1 - 3.0.5 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io-client Depends on vulnerable versions of socket.io-parser node_modules/socket.io-client iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller redis 2.6.0 - 3.1.0 Potential exponential regex in monitor mode - https://github.com/advisories/GHSA-35q2-47q7-3pc3 fix available via `npm audit fix` node_modules/redis iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller socket.io <=2.4.1 Severity: high Insecure defaults due to CORS misconfiguration in socket.io - https://github.com/advisories/GHSA-fxwf-4rqh-v8g3 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io Depends on vulnerable versions of socket.io-parser fix available via `npm audit fix` node_modules/socket.io iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller socket.io-parser <=3.3.1 Severity: high Resource exhaustion in socket.io-parser - https://github.com/advisories/GHSA-xfhh-g9f5-x4m4 Depends on vulnerable versions of debug fix available via `npm audit fix` node_modules/socket.io-parser socket.io <=2.4.1 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io Depends on vulnerable versions of socket.io-parser node_modules/socket.io iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller socket.io-adapter <=1.1.0 Depends on vulnerable versions of debug Depends on vulnerable versions of socket.io-parser node_modules/socket.io-adapter socket.io-client 1.0.0-pre - 2.1.1 || 2.3.0 - 2.3.1 || 3.0.0-rc1 - 3.0.5 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io-client Depends on vulnerable versions of socket.io-parser node_modules/socket.io-client ws <=1.1.4 Severity: high Denial of Service in ws - https://github.com/advisories/GHSA-5v72-xg48-5rpm fix available via `npm audit fix` node_modules/engine.io-client/node_modules/ws node_modules/engine.io/node_modules/ws engine.io <=4.0.0-alpha.1 Depends on vulnerable versions of debug Depends on vulnerable versions of ws node_modules/engine.io socket.io <=2.4.1 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io Depends on vulnerable versions of socket.io-parser node_modules/socket.io iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller engine.io-client <=3.3.2 || 3.4.0 - 3.5.1 || 4.0.0-alpha.0 - 4.1.3 Depends on vulnerable versions of debug Depends on vulnerable versions of parsejson Depends on vulnerable versions of ws Depends on vulnerable versions of xmlhttprequest-ssl node_modules/engine.io-client socket.io-client 1.0.0-pre - 2.1.1 || 2.3.0 - 2.3.1 || 3.0.0-rc1 - 3.0.5 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io-client Depends on vulnerable versions of socket.io-parser node_modules/socket.io-client xmlhttprequest-ssl <=1.6.1 Severity: critical Improper Certificate Validation in xmlhttprequest-ssl - https://github.com/advisories/GHSA-72mh-269x-7mh5 Arbitrary Code Injection - https://github.com/advisories/GHSA-h4j5-c7cj-74xg fix available via `npm audit fix` node_modules/xmlhttprequest-ssl engine.io-client <=3.3.2 || 3.4.0 - 3.5.1 || 4.0.0-alpha.0 - 4.1.3 Depends on vulnerable versions of debug Depends on vulnerable versions of parsejson Depends on vulnerable versions of ws Depends on vulnerable versions of xmlhttprequest-ssl node_modules/engine.io-client socket.io-client 1.0.0-pre - 2.1.1 || 2.3.0 - 2.3.1 || 3.0.0-rc1 - 3.0.5 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io-client Depends on vulnerable versions of socket.io-parser node_modules/socket.io-client iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller yargs-parser 6.0.0 - 13.1.1 Severity: moderate Prototype Pollution in yargs-parser - https://github.com/advisories/GHSA-p9pc-299p-vxgp fix available via `npm audit fix` node_modules/yargs-parser yargs 8.0.0-candidate.0 - 15.0.0 Depends on vulnerable versions of cliui Depends on vulnerable versions of yargs-parser node_modules/yargs iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller 21 vulnerabilities (2 low, 9 moderate, 7 high, 3 critical) To address all issues, run: npm audit fixbedeutet das ein npm audit fix ausführen?
@feinfinger sagte in js-controller 4.0.x jetzt für alle User im STABLE!:
root@ioBroker
Und hüpf da nicht als root rum.
-
@feinfinger sagte in js-controller 4.0.x jetzt für alle User im STABLE!:
bedeutet das ein npm audit fix ausführen?
NEIN..
und stell dich mal richtig hin
cd /opt/iobroker npm i iobroker.js-controller@4.0.18 --productionund erst dann
wobei mach direkt die .19 drauf
npm i iobroker.js-controller@4.0.19 --productionDanke für die Hilfe, aber da ist wohl mehr im Busch.
Frage mich, warum updates bisher immer geklappt haben?
root@ioBroker:/opt/iobroker# npm i iobroker.js-controller@4.0.19 --production npm ERR! code ENOTEMPTY npm ERR! syscall rename npm ERR! path /opt/iobroker/node_modules/abab npm ERR! dest /opt/iobroker/node_modules/.abab-bvmibCm3 npm ERR! errno -39 npm ERR! ENOTEMPTY: directory not empty, rename '/opt/iobroker/node_modules/abab' -> '/opt/iobroker/node_modules/.abab-bvmibCm3' npm ERR! A complete log of this run can be found in: npm ERR! /home/iobroker/.npm/_logs/2022-03-07T08_39_26_200Z-debug-0.log -
Danke für die Hilfe, aber da ist wohl mehr im Busch.
Frage mich, warum updates bisher immer geklappt haben?
root@ioBroker:/opt/iobroker# npm i iobroker.js-controller@4.0.19 --production npm ERR! code ENOTEMPTY npm ERR! syscall rename npm ERR! path /opt/iobroker/node_modules/abab npm ERR! dest /opt/iobroker/node_modules/.abab-bvmibCm3 npm ERR! errno -39 npm ERR! ENOTEMPTY: directory not empty, rename '/opt/iobroker/node_modules/abab' -> '/opt/iobroker/node_modules/.abab-bvmibCm3' npm ERR! A complete log of this run can be found in: npm ERR! /home/iobroker/.npm/_logs/2022-03-07T08_39_26_200Z-debug-0.log@feinfinger sagte in js-controller 4.0.x jetzt für alle User im STABLE!:
directory not empty, rename '/opt/iobroker/node_modules/abab' -> '/opt/iobroker/node_modules/.abab-bvmibCm3'
Dann mach das doch mal.
-
@feinfinger sagte in js-controller 4.0.x jetzt für alle User im STABLE!:
directory not empty, rename '/opt/iobroker/node_modules/abab' -> '/opt/iobroker/node_modules/.abab-bvmibCm3'
Dann mach das doch mal.
Dann kommt der nächste Fehler...
root@ioBroker:/opt/iobroker# npm i iobroker.js-controller@4.0.19 --production npm ERR! code ENOTEMPTY npm ERR! syscall rename npm ERR! path /opt/iobroker/node_modules/abbrev npm ERR! dest /opt/iobroker/node_modules/.abbrev-5eNud0FY npm ERR! errno -39 npm ERR! ENOTEMPTY: directory not empty, rename '/opt/iobroker/node_modules/abbrev' -> '/opt/iobroker/node_modules/.abbrev-5eNud0FY'Was mich wundert ist, das diese Ordner alle vorhanden sind...