NEWS
PH-Messung
-
@apollon77 Hm. Davon hab ich leider keine Ahnung. Vieleicht kennt sich ja jemand damit aus.
Ich denke , wenn man den ESP auslesen könnte und dann die IP auf den Mqtt umändert , die Firmware wieder zurückspielt
dann solllte man die Daten haben. Nur auslesen kann ich auch nicht:confused:@chaosbrother sagte in PH-Messung:
Nur auslesen kann ich auch nicht
das ist auch Sinn der Sache.
Sonst könnte man deine Wettersenoren aus dem Garten klauen und hätte deine WLAN-Zugangsdaten -
Hi. My german skills are very limited but I belive I have a similar idea as you ask for.
I have a PH-803w connected and can read values in the accompanied app but that is about it.
What I would like is to publish this data to my MQTT broker and make use of it in a bigger IoT network. I.e. show it in my control panel for the entire home, or only allow chlorine dosing while the filter pump is running.When opening the device there is two pins from the ESP exposed, Rx/Tx, but yet I have not been able to read any data from them that makes sense. Normally those would be the flash program pins and debug logging and use serial interface. But regardless of Baudrate I try on my UART cable it seem only to be random values. More attempts to come, yet only look at it as ASCII, binary data is also a possibility.
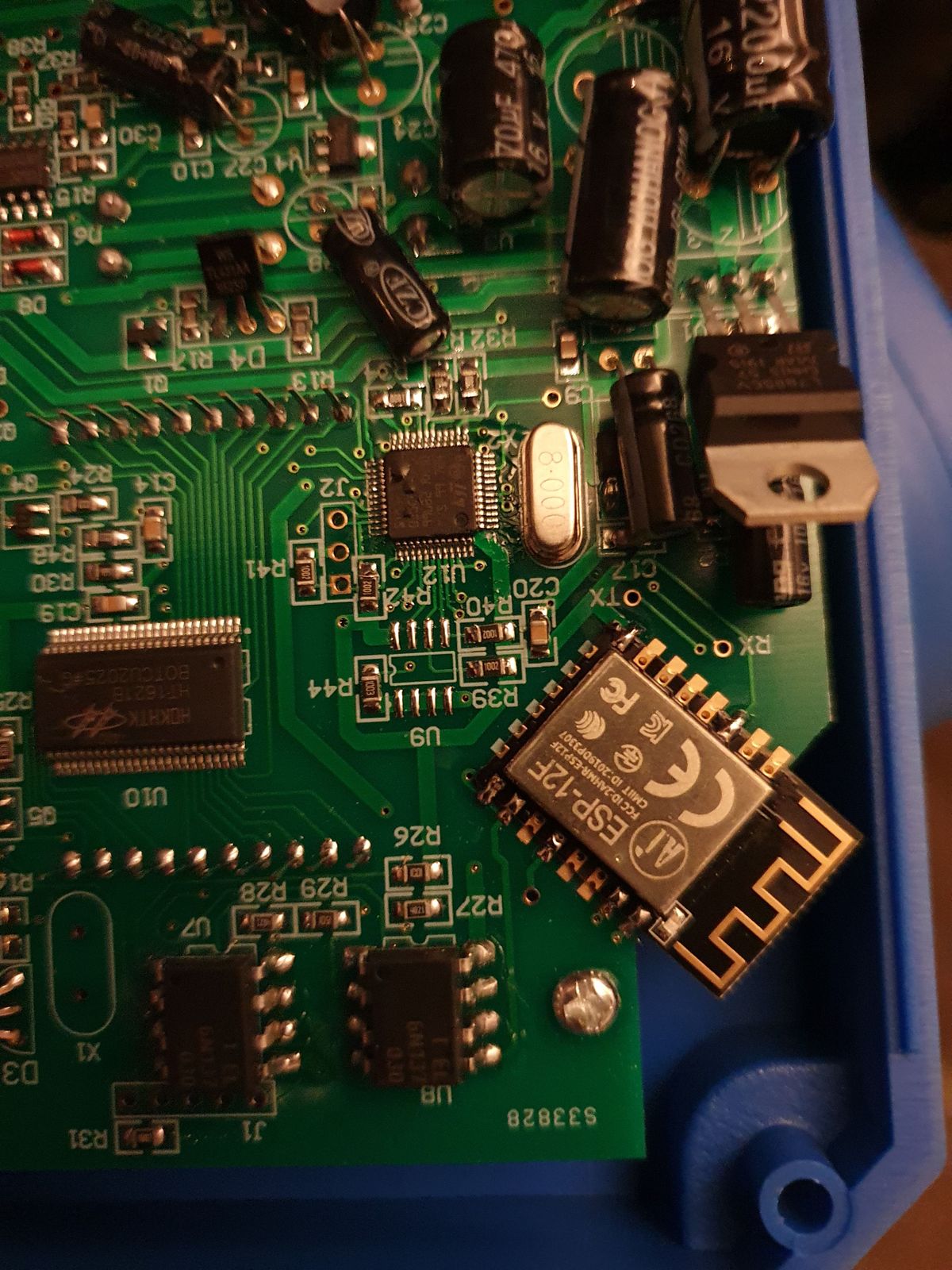
Next way to tackle it is to connect the device over an network bridge (device <-> router <-> bridge <-> internet) with Wireshark or similar to sniff the traffic. At least it will expose the IP ports it used in the cloud communication, but likely the data will be over a secured socket and I'm stuck.
Feel free to comment my ideas or add new.
@dala
Hi,
Sorry for writing in English, I don't speak German.
I found this thread while Googling for PH-803W firmware flashes...Some background:
I'm in the process of buying a Wifi PH/ORP measurement tool and found PH-803W on AliBaba. I wanted to check a way to not use the Android App, but redirect the data from PH-803W to a MQTT broker and then integrate with my home automation system. I use HomeSeer for home automation.According to the picture posted by you the PH-803W uses ESP12f chip, which is based on ESP8266 chipset.
Have to tries to use tools like Tasmota or similar to reflash the device?There are many toolkits that support ESP8266 firmware rewrite. Take a look:
https://en.wikipedia.org/wiki/ESP8266#Espressif_modules -
Bei mir steht das Thema auch an ... Blöd das da Lokal nix geht :-(
Aber DNS umbiegen ist echt blöd und unconvenient :-(Hat jemand die App schonmal auseinander genommen das man die Daten da abholen kann wenigstens?
@apollon77 hab ich doch vorhin im poolpower forum deinen Alias entdeckt ;-)
Ich bin da jetzt auch noch nicht wirklich weiter mit dem Teil. An App zerlegen hab ich auch schon gedacht, braucht nur jemanden, der es kann.
Ich weiß nicht, ob man auch an RX/TX was auslesen könnte von dem ESP. -
@apollon77 hab ich doch vorhin im poolpower forum deinen Alias entdeckt ;-)
Ich bin da jetzt auch noch nicht wirklich weiter mit dem Teil. An App zerlegen hab ich auch schon gedacht, braucht nur jemanden, der es kann.
Ich weiß nicht, ob man auch an RX/TX was auslesen könnte von dem ESP.@coyote sagte in PH-Messung:
An App zerlegen hab ich auch schon gedacht, braucht nur jemanden, der es kann.
naja da muss man mal schauen. Ich würde mit nem HTTP proxy anfangen und schauen ob man HTTP requests sieht ... wenn nein muss man mit wireshark ran dann könnte es MQTT sein.
Also wenn du die app und nen clpud account hast mir mal schicken mit den Daten und ich schaue mal :-)
-
@coyote sagte in PH-Messung:
An App zerlegen hab ich auch schon gedacht, braucht nur jemanden, der es kann.
naja da muss man mal schauen. Ich würde mit nem HTTP proxy anfangen und schauen ob man HTTP requests sieht ... wenn nein muss man mit wireshark ran dann könnte es MQTT sein.
Also wenn du die app und nen clpud account hast mir mal schicken mit den Daten und ich schaue mal :-)
@apollon77 mit http proxy kann ich nix anfangen, weiß ich nicht wie das geht.
Wireshark hatte ich schon benutzt, damit hab ich die IP und den Port raus bekommen, die das Ding anspricht.
Nutze aber auch den Cloud Zugang nicht, nur LAN oder über VPN, wobei er in der App auch Remote anzeigt, wenn ich über VPN verbunden bin.Wenn es dir hilft, kann ich auch nen Account anlegen
-
@apollon77 mit http proxy kann ich nix anfangen, weiß ich nicht wie das geht.
Wireshark hatte ich schon benutzt, damit hab ich die IP und den Port raus bekommen, die das Ding anspricht.
Nutze aber auch den Cloud Zugang nicht, nur LAN oder über VPN, wobei er in der App auch Remote anzeigt, wenn ich über VPN verbunden bin.Wenn es dir hilft, kann ich auch nen Account anlegen
-
@coyote Ahhh ... die App verbindet ich lokal?? Ja dann ... aber ja am Ende muss man schauen was die App tut. Wenn Lokal dann braucht man wohl eher direkten Zugriff
@apollon77
Also ich weiß nicht so recht, lokal sei mal dahin gestellt. In der App steht zwar "LAN" wenn ich mit beidem im heimischen WLAN bin und wenn ich per VPN drauf zugrreife steht "Remote" in der App. Aber bei Wireshark kommen die gleichen Protokolle und auch IP Adresse raus.Schau mal, so siehts in wireshark aus.
59398 42.180687 119.29.42.117 192.168.66.54 MQTT 60 Ping Response 58392 41.859962 192.168.66.54 119.29.42.117 MQTT 56 Ping Request 56888 41.376643 192.168.66.54 119.29.42.117 MQTT 134 Publish Message [dev2app/CFqpJTSymCE9PLlp1DpbhY/usr2AiQiQhHhGgG5F5F4E4t] 55942 41.070275 119.29.42.117 192.168.66.54 MQTT 125 Publish Message [app2dev/CFqpJTSymCE9PLlp1DpbhY/usr2AiQiQhHhGgG5F5F4E4t] 55898 41.048388 192.168.66.54 119.29.42.117 MQTT 106 Publish Message [dev2app/CFqpJTSymCE9PLlp1DpbhY] 55755 41.006119 119.29.42.117 192.168.66.54 MQTT 121 Publish Message [app2dev/CFqpJTSymCE9PLlp1DpbhY/usr2AiQiQhHhGgG5F5F4E4t] 53674 40.334612 192.168.66.54 119.29.42.117 MQTT 106 Publish Message [dev2app/CFqpJTSymCE9PLlp1DpbhY] 52837 40.064017 119.29.42.117 192.168.66.54 MQTT 100 Publish Message [ser2cli_res/CFqpJTSymCE9PLlp1DpbhY] 35117 34.327664 192.168.66.54 119.29.42.117 MQTT 106 Publish Message [dev2app/CFqpJTSymCE9PLlp1DpbhY] 5944 24.840750 192.168.66.54 119.29.42.117 MQTT 106 Publish Message [dev2app/CFqpJTSymCE9PLlp1DpbhY] 917 18.835631 192.168.66.54 119.29.42.117 MQTT 106 Publish Message [dev2app/CFqpJTSymCE9PLlp1DpbhY] 397 12.827564 192.168.66.54 119.29.42.117 MQTT 106 Publish Message [dev2app/CFqpJTSymCE9PLlp1DpbhY] 123 6.535826 192.168.66.54 119.29.42.117 MQTT 106 Publish Message [dev2app/CFqpJTSymCE9PLlp1DpbhY] 9 0.532890 192.168.66.54 119.29.42.117 MQTT 106 Publish Message [dev2app/CFqpJTSymCE9PLlp1DpbhY] -
Ich switche mal auf Englisch um auch @sharan mitzunehmen:
Ok, I found some code and looks like the GizWith stuff opens ports locally on the device in LAN for port 12416 (TCP) and 12414 (UDP) and UDP Broadcast on 2415 ... So it could be really an idea to do a port scan against the device in local network.
(https://github.com/gizwits/gokit-GAgent/blob/master/software/lan/Socket.c#L109-L111)We should also see UDP packages I think which are then also used for discovery.
Also in this code some stuff is in that could describe some protocols and stuff.
So, yes also the local stuff should be a MQTT server when I interpret that correctly
https://github.com/gizwits/gokit-GAgent/blob/master/software/lan/lan.c#L291
(all relevant only if that code is somehow current) :-)
-
Ich switche mal auf Englisch um auch @sharan mitzunehmen:
Ok, I found some code and looks like the GizWith stuff opens ports locally on the device in LAN for port 12416 (TCP) and 12414 (UDP) and UDP Broadcast on 2415 ... So it could be really an idea to do a port scan against the device in local network.
(https://github.com/gizwits/gokit-GAgent/blob/master/software/lan/Socket.c#L109-L111)We should also see UDP packages I think which are then also used for discovery.
Also in this code some stuff is in that could describe some protocols and stuff.
So, yes also the local stuff should be a MQTT server when I interpret that correctly
https://github.com/gizwits/gokit-GAgent/blob/master/software/lan/lan.c#L291
(all relevant only if that code is somehow current) :-)
@apollon77 here again everything that wireshark outputs to adress 119.29.42.117
Port is 47280
I don't see UDP packets9 0.532890 192.168.66.54 119.29.42.117 MQTT 106 Publish Message [dev2app/CFqpJTSymCE9PLlp1DpbhY] 123 6.535826 192.168.66.54 119.29.42.117 MQTT 106 Publish Message [dev2app/CFqpJTSymCE9PLlp1DpbhY] 397 12.827564 192.168.66.54 119.29.42.117 MQTT 106 Publish Message [dev2app/CFqpJTSymCE9PLlp1DpbhY] 917 18.835631 192.168.66.54 119.29.42.117 MQTT 106 Publish Message [dev2app/CFqpJTSymCE9PLlp1DpbhY] 5944 24.840750 192.168.66.54 119.29.42.117 MQTT 106 Publish Message [dev2app/CFqpJTSymCE9PLlp1DpbhY] 35117 34.327664 192.168.66.54 119.29.42.117 MQTT 106 Publish Message [dev2app/CFqpJTSymCE9PLlp1DpbhY] 53057 40.134667 192.168.66.54 119.29.42.117 TCP 54 47280 → 1883 [ACK] Seq=313 Ack=47 Win=4957 Len=0 53674 40.334612 192.168.66.54 119.29.42.117 MQTT 106 Publish Message [dev2app/CFqpJTSymCE9PLlp1DpbhY] 55772 41.009306 192.168.66.54 119.29.42.117 TCP 54 47280 → 1883 [ACK] Seq=365 Ack=114 Win=4890 Len=0 55898 41.048388 192.168.66.54 119.29.42.117 MQTT 106 Publish Message [dev2app/CFqpJTSymCE9PLlp1DpbhY] 56143 41.134375 192.168.66.54 119.29.42.117 TCP 54 47280 → 1883 [ACK] Seq=417 Ack=185 Win=4819 Len=0 56888 41.376643 192.168.66.54 119.29.42.117 MQTT 134 Publish Message [dev2app/CFqpJTSymCE9PLlp1DpbhY/usr2AiQiQhHhGgG5F5F4E4t] 58392 41.859962 192.168.66.54 119.29.42.117 MQTT 56 Ping Request 59645 42.258980 192.168.66.54 119.29.42.117 TCP 54 47280 → 1883 [ACK] Seq=499 Ack=187 Win=4817 Len=0 -
In fact this all seems to be the "device to cloud" traffic ... so I would have expected that as soon as you open the app on the phone the app sends out udp packages locally and this is also answered by the device and then the app connects to the device directly ...
so you would need to check traffic where your mobile phone and the local device IP is involved
-
Hi yall, my first post so be gentle...
I connected the TX/RX inside the PH-803W with my UART to see what is shown there:
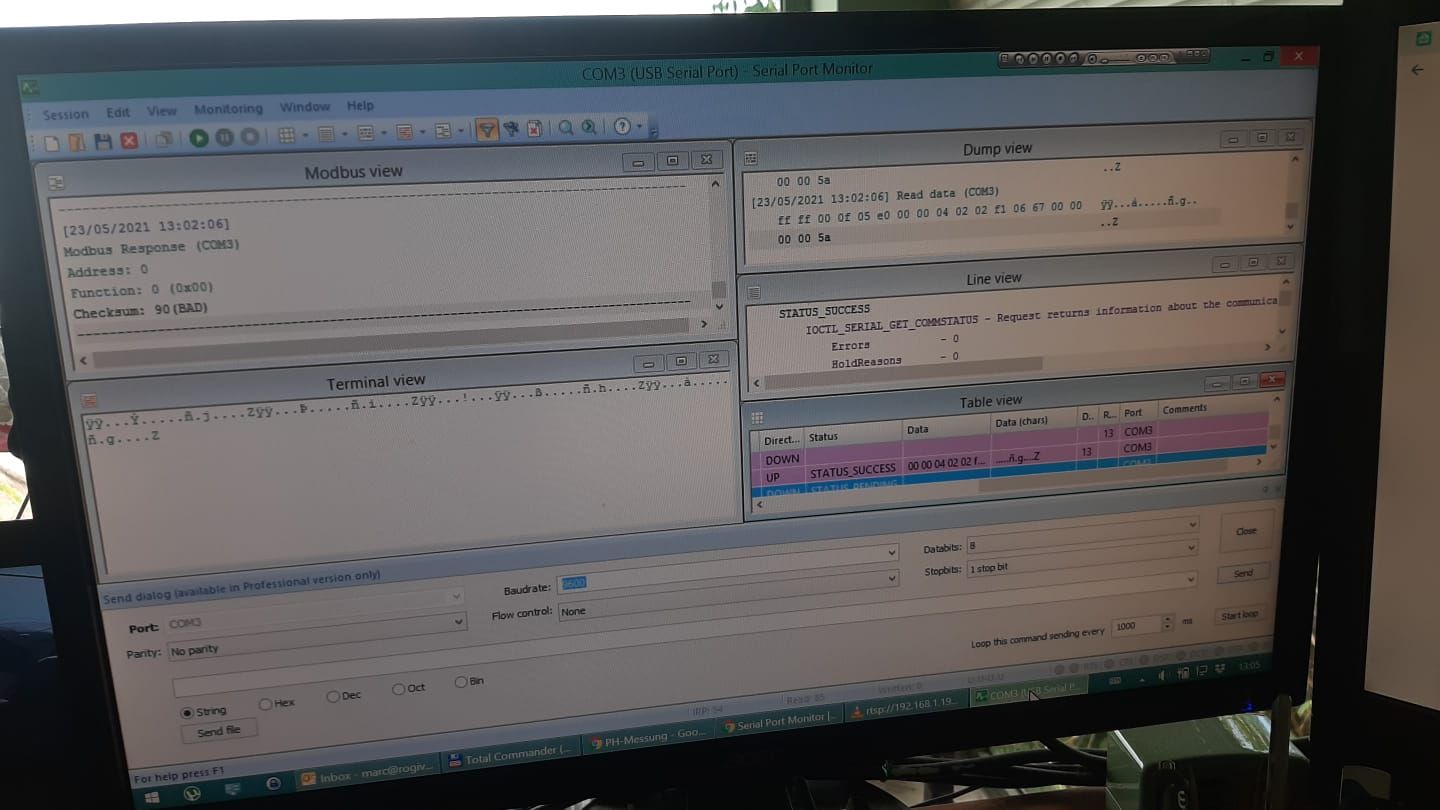
Seems it sends the same binary data that Anti was able to reroute to his MQTT? While my router has the NAT functionality, I unfortunately cannot define virtual IP addresses, so that route is not viable for me and probably most here. But if we can make sense of the TX/RX Data, we could potentially add another ESP on this port and let it send the data to where we want it to be sent?
Hope this makes sense and is helpful for the discussuion, Cheers
-
Hi, maybe it would be easier to make a backup of the firmware from the ESP and then just change the gateway and play back again. Something like that works with Esptool.py , but I don't know my way around that well either.
-
Hey,
I hope I also get my device in next 1 days (just ordered yesterday). When the code I found telling anything AND when it is right that the App also switches to "local" communication when in same WLAN then honestly I would start really analyzing that. That could be way more easy!
Code wise it seemed to me that locally the device itself acts as a simple mqtt server hopefully.So if someone wants to do stuff in between:
- maybe start with a nmap scan against the local IP ... is there anything open and what can be found there?
- start (like @coyote started) with Wireshark but focus on mobile device/App-with-ph-803w communication ... there should be some
Anyone up for that?
PS: @Marc-R
Hi yall, my first post so be gentle...
We are always :-)
To maybe see more in the data would be a good idea to also see what data the device was showing as you tried it, maybe the "calculation rules" that @Anti was able to decode also apply. ALso interesting would be which part o fthe message is changing when the values change and which part stays static. So now you need to start "data crunching", I expect the data needs to be in there
-
Hey,
I hope I also get my device in next 1 days (just ordered yesterday). When the code I found telling anything AND when it is right that the App also switches to "local" communication when in same WLAN then honestly I would start really analyzing that. That could be way more easy!
Code wise it seemed to me that locally the device itself acts as a simple mqtt server hopefully.So if someone wants to do stuff in between:
- maybe start with a nmap scan against the local IP ... is there anything open and what can be found there?
- start (like @coyote started) with Wireshark but focus on mobile device/App-with-ph-803w communication ... there should be some
Anyone up for that?
PS: @Marc-R
Hi yall, my first post so be gentle...
We are always :-)
To maybe see more in the data would be a good idea to also see what data the device was showing as you tried it, maybe the "calculation rules" that @Anti was able to decode also apply. ALso interesting would be which part o fthe message is changing when the values change and which part stays static. So now you need to start "data crunching", I expect the data needs to be in there
Today I made a local scan in the same network. At the first attempt it was over the VPN connection and therefore "Remote"
Maybe you like that better @apollon77 ;-)
39484 33.259423 192.168.66.54 192.168.66.8 TCP 62 12416 → 48158 [PSH, ACK] Seq=94 Ack=83 Win=5758 Len=8 29590 29.524847 192.168.66.54 192.168.66.8 TCP 62 12416 → 48158 [PSH, ACK] Seq=86 Ack=75 Win=5766 Len=8 26127 28.341450 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 18180 25.193896 192.168.66.54 192.168.66.8 TCP 62 12416 → 48158 [PSH, ACK] Seq=78 Ack=67 Win=5774 Len=8 8826 21.298249 192.168.66.54 192.168.66.8 TCP 62 12416 → 48158 [PSH, ACK] Seq=70 Ack=59 Win=5782 Len=8 8700 21.257654 192.168.66.54 192.168.66.8 TCP 76 12416 → 48158 [PSH, ACK] Seq=48 Ack=51 Win=5790 Len=22 8696 21.255005 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 7288 20.836871 192.168.66.54 192.168.66.8 TCP 72 12416 → 48158 [PSH, ACK] Seq=30 Ack=38 Win=5803 Len=18 7287 20.824022 192.168.66.54 192.168.66.8 TCP 54 12416 → 48158 [ACK] Seq=30 Ack=38 Win=5803 Len=0 6978 20.574620 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 5694 20.118304 192.168.66.54 192.168.66.8 TCP 63 12416 → 48158 [PSH, ACK] Seq=21 Ack=29 Win=5812 Len=9 5643 20.100519 192.168.66.54 192.168.66.8 TCP 74 12416 → 48158 [PSH, ACK] Seq=1 Ack=9 Win=5832 Len=20 5607 20.088883 192.168.66.54 192.168.66.8 TCP 58 12416 → 48158 [SYN, ACK] Seq=0 Ack=1 Win=5840 Len=0 MSS=1460 3855 19.504039 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 2761 18.290828 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 2567 17.284353 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 2381 16.220137 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 2210 15.190409 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 2063 14.544840 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 1906 13.514199 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 1662 12.248355 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 -
Today I made a local scan in the same network. At the first attempt it was over the VPN connection and therefore "Remote"
Maybe you like that better @apollon77 ;-)
39484 33.259423 192.168.66.54 192.168.66.8 TCP 62 12416 → 48158 [PSH, ACK] Seq=94 Ack=83 Win=5758 Len=8 29590 29.524847 192.168.66.54 192.168.66.8 TCP 62 12416 → 48158 [PSH, ACK] Seq=86 Ack=75 Win=5766 Len=8 26127 28.341450 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 18180 25.193896 192.168.66.54 192.168.66.8 TCP 62 12416 → 48158 [PSH, ACK] Seq=78 Ack=67 Win=5774 Len=8 8826 21.298249 192.168.66.54 192.168.66.8 TCP 62 12416 → 48158 [PSH, ACK] Seq=70 Ack=59 Win=5782 Len=8 8700 21.257654 192.168.66.54 192.168.66.8 TCP 76 12416 → 48158 [PSH, ACK] Seq=48 Ack=51 Win=5790 Len=22 8696 21.255005 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 7288 20.836871 192.168.66.54 192.168.66.8 TCP 72 12416 → 48158 [PSH, ACK] Seq=30 Ack=38 Win=5803 Len=18 7287 20.824022 192.168.66.54 192.168.66.8 TCP 54 12416 → 48158 [ACK] Seq=30 Ack=38 Win=5803 Len=0 6978 20.574620 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 5694 20.118304 192.168.66.54 192.168.66.8 TCP 63 12416 → 48158 [PSH, ACK] Seq=21 Ack=29 Win=5812 Len=9 5643 20.100519 192.168.66.54 192.168.66.8 TCP 74 12416 → 48158 [PSH, ACK] Seq=1 Ack=9 Win=5832 Len=20 5607 20.088883 192.168.66.54 192.168.66.8 TCP 58 12416 → 48158 [SYN, ACK] Seq=0 Ack=1 Win=5840 Len=0 MSS=1460 3855 19.504039 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 2761 18.290828 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 2567 17.284353 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 2381 16.220137 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 2210 15.190409 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 2063 14.544840 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 1906 13.514199 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 1662 12.248355 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 -
@coyote yes. Via VPN normally all UDP messages are not transferred ;-)
Can you send me that wireshark file via email to iobroker@fischer-ka.de
Ps: i assume .54 is the ph803 and the .8 is mobile device?
@apollon77 ok, i didn't know.
Sure, think it'll take another hour, then I can send it to you.
Yes exactly. .54 is the 803W and .8 is the smartphone
-
@coyote yes. Via VPN normally all UDP messages are not transferred ;-)
Can you send me that wireshark file via email to iobroker@fischer-ka.de
Ps: i assume .54 is the ph803 and the .8 is mobile device?
@apollon77 you have mail ;-)
-
Das mal zur App vieleicht kann jemand was damit anfangen.
https://docs.gizwits.com/en-us/AppDev/AndroidSDKA2.html#5-Device-control
Dafür ist mein Englich zu schlecht. Wenn ich das richtig verstehe kann und darf man an der App was ändern mit
Android Studio -
@apollon77 you have mail ;-)
@coyote Ok, I start to collect here the stuff I saw in the Wireshark:
-
(01) App sends a UDP broadcast with data "00 00 00 03 03 00 00 03" to port 12414
-
App sends MDNS query to 224.0.0.251 _%9E5E7C8F47989526C9BCD95D24084F6F0B27C5ED._sub._googlecast._tcp.local, "QU" question PTR _googlecast._tcp.local, "QU" question
-
(02) Device Answers with UDP message from port 12414 to App
00:00:00:03:68:00:00:04:00:16:43:46:71:70:4a:54:53:79:6d:43:45:39:50:4c:6c:70:31:44:70:62:68:59:00:06:48:3f:da:87:dc:47:00:00:00:20:32:64:33:64:39:35:34:64:39:62:62:37:34:31:62:34:61:31:39:62:61:31:31:35:33:31:30:34:39:33:32:62:00:00:00:00:00:00:00:02:61:70:69:2e:67:69:7a:77:69:74:73:2e:63:6f:6d:3a:38:30:00:34:2e:30:2e:38:00
( hCFqpJTSymCE9PLlp1DpbhYH?ÚÜG 2d3d954d9bb741b4a19ba1153104932bapi.gizwits.com:804.0.8) -
App connects to device on port 12416 and Device and App communicates on that port
-
(03) App sends 00:00:00:03:03:00:00:06
-
(04) Device answers: 00:00:00:03:0f:00:00:07:00:0a:X1:X2:X3:X4:X5:X6:X7:X8:X9:X0
-
(05) App sends : 00:00:00:03:0f:00:00:08:00:0a:X1:X2:X3:X4:X5:X6:X7:X8:X9:X0
-
(06) Device answers: 00:00:00:03:04:00:00:09:00
-
(07) App sends : 00:00:00:03:04:00:00:90:02
-
(08) Device answers: 00:00:00:03:0d:00:00:91:03:00:02:dc:08:9d:00:00:00:00
-
(09) App sends : 00:00:00:03:08:00:00:93:00:00:00:04:02
-
(10) Device answers: 00:00:00:03:11:00:00:94:00:00:00:04:03:00:02:dc:08:9d:00:00:00:00
-
(11) App sends : 00:00:00:03:03:00:00:15
-
(12) Device answers: 00:00:00:03:03:00:00:16
... and the last two repeat every 4s (seems like a ping/pong)
Das passt grob spontan zu dem Protokoll von hier https://github.com/gizwits/gokit-GAgent/blob/master/software/lan/lan.c#L291
- 00 00 00 03 sind immer die lokalen ersten Bytes
- byte Nummer 8 ist das "Kommando" (also wenn App->Device) ... damit von oben
- (---) code 01 -- UDP to device - onBoarding message ... 00 XX <XX bytes ssid> 00 YY <YY bytes ssidpwd> (unsure with 00xx/yy or if only xx/yy?)
- (---) code 02 -- UDP from device - onBoarding response ... just as OK message
- (01): code 03 -- UDP to device - Discover message
- (02): code 04 ?? -- UDP from device - Discover response
- (---) code 05 ?? -- UDP from device active broadcast from device
- (03): code 06 -- TCP to device: user bind passcode; Device returns passcode for login command
- (04): code 07 -- TCP from device: device answers with data and 10 chars as passcode
- (05): code 08 -- TCP to device: user login : Device wants to see the same passcode as sent above
- (06): code 09 -- TCP from device: login result: 00=ok, 01=error
- (07): code 90 -- TCP to device: send p0 to uart ... schreibt "02" ans Device
- (08): code 91 ?? TCP answer from serial?? 03:00 02:dc 08:9d 00:00 00:00
- (09): code 93 ?? -- TCP to device - unknown 00:00:00:04:02
- (10): code 94 ?? -- TCP from device - unknown 00:00 00:04 03:00 02:dc 08:9d 00:00 00:00
- (11) code 15: -- TCP to device: "tick" aka ping
- (12) code 16: should be "pong" then
If we now would have info on the values on display vs data it would help :-)
- 02dc could be 732 with idea from above with /100 == 7,32 ... PH??
- 089d could be 2205 with idea from above -2000 === 205 ... ORP?
@coyote ??
The two other 00 00 at the end could be the switch states ... but also would need to be verified.
Ingo
-
-
@coyote Ok, I start to collect here the stuff I saw in the Wireshark:
-
(01) App sends a UDP broadcast with data "00 00 00 03 03 00 00 03" to port 12414
-
App sends MDNS query to 224.0.0.251 _%9E5E7C8F47989526C9BCD95D24084F6F0B27C5ED._sub._googlecast._tcp.local, "QU" question PTR _googlecast._tcp.local, "QU" question
-
(02) Device Answers with UDP message from port 12414 to App
00:00:00:03:68:00:00:04:00:16:43:46:71:70:4a:54:53:79:6d:43:45:39:50:4c:6c:70:31:44:70:62:68:59:00:06:48:3f:da:87:dc:47:00:00:00:20:32:64:33:64:39:35:34:64:39:62:62:37:34:31:62:34:61:31:39:62:61:31:31:35:33:31:30:34:39:33:32:62:00:00:00:00:00:00:00:02:61:70:69:2e:67:69:7a:77:69:74:73:2e:63:6f:6d:3a:38:30:00:34:2e:30:2e:38:00
( hCFqpJTSymCE9PLlp1DpbhYH?ÚÜG 2d3d954d9bb741b4a19ba1153104932bapi.gizwits.com:804.0.8) -
App connects to device on port 12416 and Device and App communicates on that port
-
(03) App sends 00:00:00:03:03:00:00:06
-
(04) Device answers: 00:00:00:03:0f:00:00:07:00:0a:X1:X2:X3:X4:X5:X6:X7:X8:X9:X0
-
(05) App sends : 00:00:00:03:0f:00:00:08:00:0a:X1:X2:X3:X4:X5:X6:X7:X8:X9:X0
-
(06) Device answers: 00:00:00:03:04:00:00:09:00
-
(07) App sends : 00:00:00:03:04:00:00:90:02
-
(08) Device answers: 00:00:00:03:0d:00:00:91:03:00:02:dc:08:9d:00:00:00:00
-
(09) App sends : 00:00:00:03:08:00:00:93:00:00:00:04:02
-
(10) Device answers: 00:00:00:03:11:00:00:94:00:00:00:04:03:00:02:dc:08:9d:00:00:00:00
-
(11) App sends : 00:00:00:03:03:00:00:15
-
(12) Device answers: 00:00:00:03:03:00:00:16
... and the last two repeat every 4s (seems like a ping/pong)
Das passt grob spontan zu dem Protokoll von hier https://github.com/gizwits/gokit-GAgent/blob/master/software/lan/lan.c#L291
- 00 00 00 03 sind immer die lokalen ersten Bytes
- byte Nummer 8 ist das "Kommando" (also wenn App->Device) ... damit von oben
- (---) code 01 -- UDP to device - onBoarding message ... 00 XX <XX bytes ssid> 00 YY <YY bytes ssidpwd> (unsure with 00xx/yy or if only xx/yy?)
- (---) code 02 -- UDP from device - onBoarding response ... just as OK message
- (01): code 03 -- UDP to device - Discover message
- (02): code 04 ?? -- UDP from device - Discover response
- (---) code 05 ?? -- UDP from device active broadcast from device
- (03): code 06 -- TCP to device: user bind passcode; Device returns passcode for login command
- (04): code 07 -- TCP from device: device answers with data and 10 chars as passcode
- (05): code 08 -- TCP to device: user login : Device wants to see the same passcode as sent above
- (06): code 09 -- TCP from device: login result: 00=ok, 01=error
- (07): code 90 -- TCP to device: send p0 to uart ... schreibt "02" ans Device
- (08): code 91 ?? TCP answer from serial?? 03:00 02:dc 08:9d 00:00 00:00
- (09): code 93 ?? -- TCP to device - unknown 00:00:00:04:02
- (10): code 94 ?? -- TCP from device - unknown 00:00 00:04 03:00 02:dc 08:9d 00:00 00:00
- (11) code 15: -- TCP to device: "tick" aka ping
- (12) code 16: should be "pong" then
If we now would have info on the values on display vs data it would help :-)
- 02dc could be 732 with idea from above with /100 == 7,32 ... PH??
- 089d could be 2205 with idea from above -2000 === 205 ... ORP?
@coyote ??
The two other 00 00 at the end could be the switch states ... but also would need to be verified.
Ingo
@apollon77 sounds good ;-)
Will do more test today with wireshark and and will write down the values from the display or take pictures.
The switches cannot be triggered manually.
The device is currently not in use by me, there are no probes connected, so the values are not directly plausible (ORP 0.2 etc.) -


