NEWS
[Gelöst] ioBroker node.js weicht von Kommandozeile ab
-
@thomas-braun sagte in ioBroker node.js weicht von Kommandozeile ab:
Und schalte die graphische Oberfläche aus.
Danke ! Wie mache ich das ? Einfach so ?
sudo systemctl set-default multi-user.targetNun kommt:
pi@raspberrypi:~ $ sudo apt install redis Paketlisten werden gelesen… Fertig Abhängigkeitsbaum wird aufgebaut… Fertig Statusinformationen werden eingelesen… Fertig Die folgenden NEUEN Pakete werden installiert: redis 0 aktualisiert, 1 neu installiert, 0 zu entfernen und 0 nicht aktualisiert. Es müssen 56,8 kB an Archiven heruntergeladen werden. Nach dieser Operation werden 67,6 kB Plattenplatz zusätzlich benutzt. Holen:1 http://deb.debian.org/debian bullseye/main arm64 redis all 5:6.0.16-1+deb11u2 [56,8 kB] Es wurden 56,8 kB in 0 s geholt (372 kB/s). Vormals nicht ausgewähltes Paket redis wird gewählt. (Lese Datenbank ... 105085 Dateien und Verzeichnisse sind derzeit installiert.) Vorbereitung zum Entpacken von .../redis_5%3a6.0.16-1+deb11u2_all.deb ... Entpacken von redis (5:6.0.16-1+deb11u2) ... redis (5:6.0.16-1+deb11u2) wird eingerichtet ... pi@raspberrypi:~ $ apt policy redis redis: Installiert: 5:6.0.16-1+deb11u2 Installationskandidat: 5:6.0.16-1+deb11u2 Versionstabelle: *** 5:6.0.16-1+deb11u2 500 500 http://deb.debian.org/debian bullseye/main arm64 Packages 500 http://deb.debian.org/debian bullseye/main armhf Packages 500 http://security.debian.org/debian-security bullseye-security/main arm64 Packages 500 http://security.debian.org/debian-security bullseye-security/main armhf Packages 100 /var/lib/dpkg/statusDie ioBroker Oberfläche kommt nach wie vor nicht...
GUI aus:
sudo raspi-configDann im Menü:
1 System Options S5 Boot / Auto Login B1 ConsoleGeht auch (linux-typisch) auf andere Arten.
-
GUI aus:
sudo raspi-configDann im Menü:
1 System Options S5 Boot / Auto Login B1 ConsoleGeht auch (linux-typisch) auf andere Arten.
@thomas-braun Ok habe ich gemacht...:)
Auch nach der Installation und dem Neustarten tut sich nichts in Sachen ioBroker Oberfläche.
pi@raspberrypi:~ $ iobroker list instances Cannot read system.config: null (OK when migrating or restoring) + instance is alive -
@thomas-braun Ok habe ich gemacht...:)
Auch nach der Installation und dem Neustarten tut sich nichts in Sachen ioBroker Oberfläche.
pi@raspberrypi:~ $ iobroker list instances Cannot read system.config: null (OK when migrating or restoring) + instance is aliveIch wollte also das zuvor erstellte Backup von GDrive über BackitUp einspielen, was auch gut aussah.
Welche Versionen waren denn im Backup drin? Hattest du das auf einen aktuellen Stand gebracht? Denn du kannst nicht einfach ein 'steinaltes Backup' in einen frischen ioBroker stopfen.
-
Ich wollte also das zuvor erstellte Backup von GDrive über BackitUp einspielen, was auch gut aussah.
Welche Versionen waren denn im Backup drin? Hattest du das auf einen aktuellen Stand gebracht? Denn du kannst nicht einfach ein 'steinaltes Backup' in einen frischen ioBroker stopfen.
@thomas-braun sagte in ioBroker node.js weicht von Kommandozeile ab:
Welche Versionen waren denn im Backup drin?
Soweit es eben ging hatte ich alle Adapter aktualisiert.
Einige haben das Update aber verweigert da js.controller >= 3.3.22 erwartet wurde.
Das war ja der Grund für das neue OS. -
@thomas-braun sagte in ioBroker node.js weicht von Kommandozeile ab:
Welche Versionen waren denn im Backup drin?
Soweit es eben ging hatte ich alle Adapter aktualisiert.
Einige haben das Update aber verweigert da js.controller >= 3.3.22 erwartet wurde.
Das war ja der Grund für das neue OS.Bei dem Abstand zwischen den js-controller-Versionen wirst du da kein Land sehen.
-
Bei dem Abstand zwischen den js-controller-Versionen wirst du da kein Land sehen.
@thomas-braun sagte
Bei dem Abstand zwischen den js-controller-Versionen wirst du da kein Land sehen.
Einzige Chance ist also neu anzufangen ?
Oder kann ich zumindest meine Scenen retten bzw auf ein neues System übertragen ?
Die alte SD Karte habe ich natürlich :) -
@thomas-braun sagte
Bei dem Abstand zwischen den js-controller-Versionen wirst du da kein Land sehen.
Einzige Chance ist also neu anzufangen ?
Oder kann ich zumindest meine Scenen retten bzw auf ein neues System übertragen ?
Die alte SD Karte habe ich natürlich :)Oder es findet sich wer anders. Ich befasse mich nicht mit so alten Versionen.
Hab also keine Erfahrung was solche Zeitreisen angeht. -
Oder es findet sich wer anders. Ich befasse mich nicht mit so alten Versionen.
Hab also keine Erfahrung was solche Zeitreisen angeht.und die js-controller-Version vor dem Update des OS irgendwie zu updaten geht nicht ?
-
und die js-controller-Version vor dem Update des OS irgendwie zu updaten geht nicht ?
@lethuer sagte in ioBroker node.js weicht von Kommandozeile ab:
und die js-controller-Version vor dem Update des OS irgendwie zu updaten geht nicht ?
Das wäre halt mein Ansatz gewesen, um diese großen Sprünge zu vermeiden.
-
@lethuer sagte in ioBroker node.js weicht von Kommandozeile ab:
und die js-controller-Version vor dem Update des OS irgendwie zu updaten geht nicht ?
Das wäre halt mein Ansatz gewesen, um diese großen Sprünge zu vermeiden.
Mein Versuch um von 3.1.6 auf 3.3.22 zu kommen hat auch nicht geklappt...
keine ahnung wie ich da noch den js-controller updaten kann um mein system zu retten.pi@ioBroker-RasPi:~$ npm install iobroker.js-controller@3.3.22 added 2 packages, removed 28 packages, changed 19 packages, and audited 281 packages in 27s 14 packages are looking for funding run `npm fund` for details 4 vulnerabilities (3 moderate, 1 high) To address all issues (including breaking changes), run: npm audit fix --force Run `npm audit` for details.pi@ioBroker-RasPi:~$ npm audit fix --force npm WARN using --force Recommended protections disabled. npm WARN audit Updating iobroker.js-controller to 4.0.23, which is a SemVer major change. added 28 packages, removed 2 packages, changed 19 packages, and audited 307 packages in 36s 18 packages are looking for funding run `npm fund` for details # npm audit report node-forge <=1.2.1 Severity: high Open Redirect in node-forge - https://github.com/advisories/GHSA-8fr3-hfg3-gpgp Prototype Pollution in node-forge debug API. - https://github.com/advisories/GHSA-5rrq-pxf6-6jx5 Prototype Pollution in node-forge util.setPath API - https://github.com/advisories/GHSA-wxgw-qj99-44c2 Prototype Pollution in node-forge - https://github.com/advisories/GHSA-92xj-mqp7-vmcj Improper Verification of Cryptographic Signature in `node-forge` - https://github.com/advisories/GHSA-2r2c-g63r-vccr Improper Verification of Cryptographic Signature in node-forge - https://github.com/advisories/GHSA-x4jg-mjrx-434g Improper Verification of Cryptographic Signature in node-forge - https://github.com/advisories/GHSA-cfm4-qjh2-4765 URL parsing in node-forge could lead to undesired behavior. - https://github.com/advisories/GHSA-gf8q-jrpm-jvxq fix available via `npm audit fix --force` Will install iobroker.js-controller@1.5.3, which is a breaking change node_modules/rsa-compat/node_modules/node-forge rsa-compat <=1.9.4 Depends on vulnerable versions of node-forge node_modules/rsa-compat le-acme-core * Depends on vulnerable versions of rsa-compat node_modules/le-acme-core iobroker.js-controller >=1.5.4 Depends on vulnerable versions of le-acme-core node_modules/iobroker.js-controller 4 vulnerabilities (3 moderate, 1 high) To address all issues (including breaking changes), run: npm audit fix --forcepi@ioBroker-RasPi:~$ npm audit fix --force npm WARN using --force Recommended protections disabled. npm WARN audit Updating iobroker.js-controller to 1.5.3, which is a SemVer major change. npm WARN deprecated json3@3.3.2: Please use the native JSON object instead of JSON 3 npm WARN deprecated mkdirp@0.5.1: Legacy versions of mkdirp are no longer supported. Please update to mkdirp 1.x. (Note that the API surface has changed to use Promises in 1.x.) added 173 packages, removed 144 packages, changed 46 packages, and audited 334 packages in 1m 14 packages are looking for funding run `npm fund` for details # npm audit report debug <2.6.9 Regular Expression Denial of Service in debug - https://github.com/advisories/GHSA-gxpj-cx7g-858c fix available via `npm audit fix --force` Will install iobroker.js-controller@4.0.23, which is a breaking change node_modules/engine.io-client/node_modules/debug node_modules/engine.io/node_modules/debug node_modules/socket.io-adapter/node_modules/debug node_modules/socket.io-client/node_modules/debug node_modules/socket.io-parser/node_modules/debug node_modules/socket.io/node_modules/debug engine.io <=3.5.0 Depends on vulnerable versions of debug Depends on vulnerable versions of ws node_modules/engine.io socket.io <=2.4.1 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io Depends on vulnerable versions of socket.io-adapter Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of socket.io-parser node_modules/socket.io iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller engine.io-client <=3.3.2 || 3.4.0 - 3.5.1 || 4.0.0-alpha.0 - 4.1.3 Depends on vulnerable versions of debug Depends on vulnerable versions of parsejson Depends on vulnerable versions of ws Depends on vulnerable versions of xmlhttprequest-ssl node_modules/engine.io-client socket.io-client 1.0.0-pre - 2.1.1 || 2.3.0 - 2.3.1 || 3.0.0-rc1 - 3.0.5 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io-client Depends on vulnerable versions of socket.io-parser node_modules/socket.io-client socket.io-adapter <=1.1.0 Depends on vulnerable versions of debug Depends on vulnerable versions of socket.io-parser node_modules/socket.io-adapter socket.io-parser <=3.3.2 Depends on vulnerable versions of debug node_modules/socket.io-parser minimist <=1.2.5 Severity: critical Prototype Pollution in minimist - https://github.com/advisories/GHSA-xvch-5gv4-984h Prototype Pollution in minimist - https://github.com/advisories/GHSA-vh95-rmgr-6w4m fix available via `npm audit fix --force` Will install iobroker.js-controller@4.0.23, which is a breaking change node_modules/winston-daily-rotate-file/node_modules/minimist mkdirp 0.4.1 - 0.5.1 Depends on vulnerable versions of minimist node_modules/winston-daily-rotate-file/node_modules/mkdirp winston-daily-rotate-file 1.7.0 - 1.7.2 Depends on vulnerable versions of mkdirp node_modules/winston-daily-rotate-file parsejson * Severity: high Regular Expression Denial of Service in parsejson - https://github.com/advisories/GHSA-q75g-2496-mxpp fix available via `npm audit fix --force` Will install iobroker.js-controller@4.0.23, which is a breaking change node_modules/parsejson redis 2.6.0 - 3.1.0 Severity: high Node-Redis potential exponential regex in monitor mode - https://github.com/advisories/GHSA-35q2-47q7-3pc3 fix available via `npm audit fix --force` Will install iobroker.js-controller@4.0.23, which is a breaking change node_modules/redis ws <=1.1.4 Severity: high Denial of Service in ws - https://github.com/advisories/GHSA-5v72-xg48-5rpm fix available via `npm audit fix --force` Will install iobroker.js-controller@4.0.23, which is a breaking change node_modules/engine.io-client/node_modules/ws node_modules/engine.io/node_modules/ws xmlhttprequest-ssl <=1.6.1 Severity: critical Improper Certificate Validation in xmlhttprequest-ssl - https://github.com/advisories/GHSA-72mh-269x-7mh5 Arbitrary Code Injection - https://github.com/advisories/GHSA-h4j5-c7cj-74xg fix available via `npm audit fix --force` Will install iobroker.js-controller@4.0.23, which is a breaking change node_modules/xmlhttprequest-ssl yargs-parser 6.0.0 - 13.1.1 Severity: moderate yargs-parser Vulnerable to Prototype Pollution - https://github.com/advisories/GHSA-p9pc-299p-vxgp fix available via `npm audit fix --force` Will install iobroker.js-controller@4.0.23, which is a breaking change node_modules/yargs-parser yargs 8.0.0-candidate.0 - 12.0.5 Depends on vulnerable versions of yargs-parser node_modules/yargs 17 vulnerabilities (1 low, 4 moderate, 7 high, 5 critical) To address issues that do not require attention, run: npm audit fix To address all issues (including breaking changes), run: npm audit fix --force -
Mein Versuch um von 3.1.6 auf 3.3.22 zu kommen hat auch nicht geklappt...
keine ahnung wie ich da noch den js-controller updaten kann um mein system zu retten.pi@ioBroker-RasPi:~$ npm install iobroker.js-controller@3.3.22 added 2 packages, removed 28 packages, changed 19 packages, and audited 281 packages in 27s 14 packages are looking for funding run `npm fund` for details 4 vulnerabilities (3 moderate, 1 high) To address all issues (including breaking changes), run: npm audit fix --force Run `npm audit` for details.pi@ioBroker-RasPi:~$ npm audit fix --force npm WARN using --force Recommended protections disabled. npm WARN audit Updating iobroker.js-controller to 4.0.23, which is a SemVer major change. added 28 packages, removed 2 packages, changed 19 packages, and audited 307 packages in 36s 18 packages are looking for funding run `npm fund` for details # npm audit report node-forge <=1.2.1 Severity: high Open Redirect in node-forge - https://github.com/advisories/GHSA-8fr3-hfg3-gpgp Prototype Pollution in node-forge debug API. - https://github.com/advisories/GHSA-5rrq-pxf6-6jx5 Prototype Pollution in node-forge util.setPath API - https://github.com/advisories/GHSA-wxgw-qj99-44c2 Prototype Pollution in node-forge - https://github.com/advisories/GHSA-92xj-mqp7-vmcj Improper Verification of Cryptographic Signature in `node-forge` - https://github.com/advisories/GHSA-2r2c-g63r-vccr Improper Verification of Cryptographic Signature in node-forge - https://github.com/advisories/GHSA-x4jg-mjrx-434g Improper Verification of Cryptographic Signature in node-forge - https://github.com/advisories/GHSA-cfm4-qjh2-4765 URL parsing in node-forge could lead to undesired behavior. - https://github.com/advisories/GHSA-gf8q-jrpm-jvxq fix available via `npm audit fix --force` Will install iobroker.js-controller@1.5.3, which is a breaking change node_modules/rsa-compat/node_modules/node-forge rsa-compat <=1.9.4 Depends on vulnerable versions of node-forge node_modules/rsa-compat le-acme-core * Depends on vulnerable versions of rsa-compat node_modules/le-acme-core iobroker.js-controller >=1.5.4 Depends on vulnerable versions of le-acme-core node_modules/iobroker.js-controller 4 vulnerabilities (3 moderate, 1 high) To address all issues (including breaking changes), run: npm audit fix --forcepi@ioBroker-RasPi:~$ npm audit fix --force npm WARN using --force Recommended protections disabled. npm WARN audit Updating iobroker.js-controller to 1.5.3, which is a SemVer major change. npm WARN deprecated json3@3.3.2: Please use the native JSON object instead of JSON 3 npm WARN deprecated mkdirp@0.5.1: Legacy versions of mkdirp are no longer supported. Please update to mkdirp 1.x. (Note that the API surface has changed to use Promises in 1.x.) added 173 packages, removed 144 packages, changed 46 packages, and audited 334 packages in 1m 14 packages are looking for funding run `npm fund` for details # npm audit report debug <2.6.9 Regular Expression Denial of Service in debug - https://github.com/advisories/GHSA-gxpj-cx7g-858c fix available via `npm audit fix --force` Will install iobroker.js-controller@4.0.23, which is a breaking change node_modules/engine.io-client/node_modules/debug node_modules/engine.io/node_modules/debug node_modules/socket.io-adapter/node_modules/debug node_modules/socket.io-client/node_modules/debug node_modules/socket.io-parser/node_modules/debug node_modules/socket.io/node_modules/debug engine.io <=3.5.0 Depends on vulnerable versions of debug Depends on vulnerable versions of ws node_modules/engine.io socket.io <=2.4.1 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io Depends on vulnerable versions of socket.io-adapter Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of socket.io-parser node_modules/socket.io iobroker.js-controller <=2.1.1 Depends on vulnerable versions of redis Depends on vulnerable versions of socket.io Depends on vulnerable versions of socket.io-client Depends on vulnerable versions of winston-daily-rotate-file Depends on vulnerable versions of yargs node_modules/iobroker.js-controller engine.io-client <=3.3.2 || 3.4.0 - 3.5.1 || 4.0.0-alpha.0 - 4.1.3 Depends on vulnerable versions of debug Depends on vulnerable versions of parsejson Depends on vulnerable versions of ws Depends on vulnerable versions of xmlhttprequest-ssl node_modules/engine.io-client socket.io-client 1.0.0-pre - 2.1.1 || 2.3.0 - 2.3.1 || 3.0.0-rc1 - 3.0.5 Depends on vulnerable versions of debug Depends on vulnerable versions of engine.io-client Depends on vulnerable versions of socket.io-parser node_modules/socket.io-client socket.io-adapter <=1.1.0 Depends on vulnerable versions of debug Depends on vulnerable versions of socket.io-parser node_modules/socket.io-adapter socket.io-parser <=3.3.2 Depends on vulnerable versions of debug node_modules/socket.io-parser minimist <=1.2.5 Severity: critical Prototype Pollution in minimist - https://github.com/advisories/GHSA-xvch-5gv4-984h Prototype Pollution in minimist - https://github.com/advisories/GHSA-vh95-rmgr-6w4m fix available via `npm audit fix --force` Will install iobroker.js-controller@4.0.23, which is a breaking change node_modules/winston-daily-rotate-file/node_modules/minimist mkdirp 0.4.1 - 0.5.1 Depends on vulnerable versions of minimist node_modules/winston-daily-rotate-file/node_modules/mkdirp winston-daily-rotate-file 1.7.0 - 1.7.2 Depends on vulnerable versions of mkdirp node_modules/winston-daily-rotate-file parsejson * Severity: high Regular Expression Denial of Service in parsejson - https://github.com/advisories/GHSA-q75g-2496-mxpp fix available via `npm audit fix --force` Will install iobroker.js-controller@4.0.23, which is a breaking change node_modules/parsejson redis 2.6.0 - 3.1.0 Severity: high Node-Redis potential exponential regex in monitor mode - https://github.com/advisories/GHSA-35q2-47q7-3pc3 fix available via `npm audit fix --force` Will install iobroker.js-controller@4.0.23, which is a breaking change node_modules/redis ws <=1.1.4 Severity: high Denial of Service in ws - https://github.com/advisories/GHSA-5v72-xg48-5rpm fix available via `npm audit fix --force` Will install iobroker.js-controller@4.0.23, which is a breaking change node_modules/engine.io-client/node_modules/ws node_modules/engine.io/node_modules/ws xmlhttprequest-ssl <=1.6.1 Severity: critical Improper Certificate Validation in xmlhttprequest-ssl - https://github.com/advisories/GHSA-72mh-269x-7mh5 Arbitrary Code Injection - https://github.com/advisories/GHSA-h4j5-c7cj-74xg fix available via `npm audit fix --force` Will install iobroker.js-controller@4.0.23, which is a breaking change node_modules/xmlhttprequest-ssl yargs-parser 6.0.0 - 13.1.1 Severity: moderate yargs-parser Vulnerable to Prototype Pollution - https://github.com/advisories/GHSA-p9pc-299p-vxgp fix available via `npm audit fix --force` Will install iobroker.js-controller@4.0.23, which is a breaking change node_modules/yargs-parser yargs 8.0.0-candidate.0 - 12.0.5 Depends on vulnerable versions of yargs-parser node_modules/yargs 17 vulnerabilities (1 low, 4 moderate, 7 high, 5 critical) To address issues that do not require attention, run: npm audit fix To address all issues (including breaking changes), run: npm audit fix --force@lethuer sagte in ioBroker node.js weicht von Kommandozeile ab:
npm audit fix --force
Finger weg! Das kramt dir alles auf links.
-
@lethuer sagte in ioBroker node.js weicht von Kommandozeile ab:
npm audit fix --force
Finger weg! Das kramt dir alles auf links.
@thomas-braun
jetzt wollte ich gerade das ding für tot erklären und auf einmal wird mir nach dem starten von ioBroker im Host js controller 3.3.22 angezeigt ! :+1: -
@thomas-braun
jetzt wollte ich gerade das ding für tot erklären und auf einmal wird mir nach dem starten von ioBroker im Host js controller 3.3.22 angezeigt ! :+1:@lethuer sagte in ioBroker node.js weicht von Kommandozeile ab:
@thomas-braun
jetzt wollte ich gerade das ding für tot erklären und auf einmal wird mir nach dem starten von ioBroker im Host js controller 3.3.22 angezeigt ! :+1:Yeah ! Kurz vor Abbruch und dann gehts doch auf einmal :) Bin happy !
Damit konnte ich jetzt zumindest schon mal alle Adapter auf den aktuellen Stand bringen.
Mit admin 6.2.23 statt 4.x.x sieht das ganze nun auch moderner aus :)
Jetzt mach ich von dem Stand noch ein Backup mit aktualisierten Adaptern.Dann versuche ich den js-controller auf den neuesten Stand zu bringen.
Dann nochmal Backup.
Dann das Ding komplett platt und eine frische Installation.
Hoffentlich klappt das Einspielen vom Backup dann. -
@lethuer sagte in ioBroker node.js weicht von Kommandozeile ab:
@thomas-braun
jetzt wollte ich gerade das ding für tot erklären und auf einmal wird mir nach dem starten von ioBroker im Host js controller 3.3.22 angezeigt ! :+1:Yeah ! Kurz vor Abbruch und dann gehts doch auf einmal :) Bin happy !
Damit konnte ich jetzt zumindest schon mal alle Adapter auf den aktuellen Stand bringen.
Mit admin 6.2.23 statt 4.x.x sieht das ganze nun auch moderner aus :)
Jetzt mach ich von dem Stand noch ein Backup mit aktualisierten Adaptern.Dann versuche ich den js-controller auf den neuesten Stand zu bringen.
Dann nochmal Backup.
Dann das Ding komplett platt und eine frische Installation.
Hoffentlich klappt das Einspielen vom Backup dann.@lethuer sagte in ioBroker node.js weicht von Kommandozeile ab:
Dann versuche ich den js-controller auf den neuesten Stand zu bringen.
Dann nochmal Backup.Das hat auch geklappt ! Jetzt habe ich also js-controller 4.0.23 :)
pi@ioBroker-RasPi:~$ iobroker upgrade self Update js-controller from @3.3.22 to @4.0.23 NPM version: 9.1.1 npm install iobroker.js-controller@4.0.23 --loglevel error --unsafe-perm --prefix "/opt/iobroker" (System call) Server Objects 127.0.0.1:54180 Error from InMemDB: Error: GET-UNSUPPORTED for namespace cfg.: Data=["meta.objects.features.useSets"] Server Objects 127.0.0.1:54180 Error from InMemDB: Error: GET-UNSUPPORTED for namespace cfg.: Data=["meta.objects.protocolVersion"] Server Objects 127.0.0.1:54180 Error from InMemDB: Error: Unknown LUA script load Server Objects 127.0.0.1:54180 Error from InMemDB: Error: Unknown LUA script load Server Objects 127.0.0.1:54180 Error from InMemDB: Error: Unknown LUA script load Server Objects 127.0.0.1:54180 Error from InMemDB: Error: SET-UNSUPPORTED for namespace cfg.: Data=["meta.objects.features.useSets",{"type":"Buffer","data":[49]}] pi@ioBroker-RasPi:~$ sudo iobroker start Starting iobroker controller daemon...Jetzt noch das OS update auf Bullseye und ich bin wieder up to date ;)
-
@lethuer sagte in ioBroker node.js weicht von Kommandozeile ab:
Dann versuche ich den js-controller auf den neuesten Stand zu bringen.
Dann nochmal Backup.Das hat auch geklappt ! Jetzt habe ich also js-controller 4.0.23 :)
pi@ioBroker-RasPi:~$ iobroker upgrade self Update js-controller from @3.3.22 to @4.0.23 NPM version: 9.1.1 npm install iobroker.js-controller@4.0.23 --loglevel error --unsafe-perm --prefix "/opt/iobroker" (System call) Server Objects 127.0.0.1:54180 Error from InMemDB: Error: GET-UNSUPPORTED for namespace cfg.: Data=["meta.objects.features.useSets"] Server Objects 127.0.0.1:54180 Error from InMemDB: Error: GET-UNSUPPORTED for namespace cfg.: Data=["meta.objects.protocolVersion"] Server Objects 127.0.0.1:54180 Error from InMemDB: Error: Unknown LUA script load Server Objects 127.0.0.1:54180 Error from InMemDB: Error: Unknown LUA script load Server Objects 127.0.0.1:54180 Error from InMemDB: Error: Unknown LUA script load Server Objects 127.0.0.1:54180 Error from InMemDB: Error: SET-UNSUPPORTED for namespace cfg.: Data=["meta.objects.features.useSets",{"type":"Buffer","data":[49]}] pi@ioBroker-RasPi:~$ sudo iobroker start Starting iobroker controller daemon...Jetzt noch das OS update auf Bullseye und ich bin wieder up to date ;)
Wie kommst du denn jetzt an npm9? Das ist noch nicht mit einer nodejs-Version released worden.
-
Wie kommst du denn jetzt an npm9? Das ist noch nicht mit einer nodejs-Version released worden.
@thomas-braun sagte in ioBroker node.js weicht von Kommandozeile ab:
Wie kommst du denn jetzt an npm9? Das ist noch nicht mit einer nodejs-Version released worden.
ich kann nur vermutungen anstellen... aber wird wohl durch das gekommen sein ?
npm audit fix npm audit fix --force -
@lethuer sagte in ioBroker node.js weicht von Kommandozeile ab:
@thomas-braun
jetzt wollte ich gerade das ding für tot erklären und auf einmal wird mir nach dem starten von ioBroker im Host js controller 3.3.22 angezeigt ! :+1:Yeah ! Kurz vor Abbruch und dann gehts doch auf einmal :) Bin happy !
Damit konnte ich jetzt zumindest schon mal alle Adapter auf den aktuellen Stand bringen.
Mit admin 6.2.23 statt 4.x.x sieht das ganze nun auch moderner aus :)
Jetzt mach ich von dem Stand noch ein Backup mit aktualisierten Adaptern.Dann versuche ich den js-controller auf den neuesten Stand zu bringen.
Dann nochmal Backup.
Dann das Ding komplett platt und eine frische Installation.
Hoffentlich klappt das Einspielen vom Backup dann.@lethuer sagte in ioBroker node.js weicht von Kommandozeile ab:
Dann das Ding komplett platt und eine frische Installation.
Hoffentlich klappt das Einspielen vom Backup dann.Dabei habe ich jetzt dann doch wieder ein Problem...
Nach dem Einspielen vom Backup aus GDrive ist die Oberfläche wieder nicht erreichbar.
Das Backup selber hatte Erfolg gemeldet und dann den Ladebalken nicht weg gemacht.
Also habe ich zumindest ein mal neu gestartet.
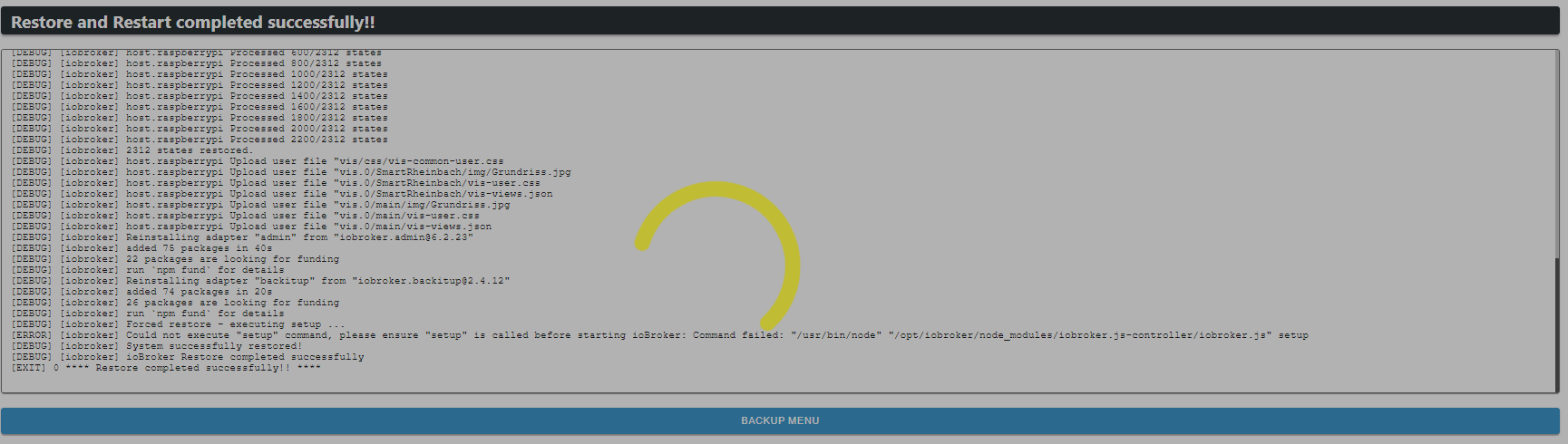
pi@raspberrypi:~ $ iobroker list instances No connection to states 127.0.0.1:6379[redis] pi@raspberrypi:~ $ apt policy redis redis: Installed: (none) Candidate: 5:6.0.16-1+deb11u2 Version table: 5:6.0.16-1+deb11u2 500 500 http://deb.debian.org/debian bullseye/main arm64 Packages 500 http://deb.debian.org/debian bullseye/main armhf Packages 500 http://security.debian.org/debian-security bullseye-security/main arm64 Packages 500 http://security.debian.org/debian-security bullseye-security/main armhf Packages -
@lethuer sagte in ioBroker node.js weicht von Kommandozeile ab:
Dann das Ding komplett platt und eine frische Installation.
Hoffentlich klappt das Einspielen vom Backup dann.Dabei habe ich jetzt dann doch wieder ein Problem...
Nach dem Einspielen vom Backup aus GDrive ist die Oberfläche wieder nicht erreichbar.
Das Backup selber hatte Erfolg gemeldet und dann den Ladebalken nicht weg gemacht.
Also habe ich zumindest ein mal neu gestartet.

pi@raspberrypi:~ $ iobroker list instances No connection to states 127.0.0.1:6379[redis] pi@raspberrypi:~ $ apt policy redis redis: Installed: (none) Candidate: 5:6.0.16-1+deb11u2 Version table: 5:6.0.16-1+deb11u2 500 500 http://deb.debian.org/debian bullseye/main arm64 Packages 500 http://deb.debian.org/debian bullseye/main armhf Packages 500 http://security.debian.org/debian-security bullseye-security/main arm64 Packages 500 http://security.debian.org/debian-security bullseye-security/main armhf PackagesNach der Installation von redis konnte ich jetzt wenigstens meine Adapter alle wieder sehen.
Irgendwas vom Backup ist also da, nur sind die meisten Adapter disabled.
I konnte die jetzt nacheinander wieder aktivieren, nur dauerte das bei manchen etwas und auch mehrere Versuche...Scheint nun aber alles geklappt zu haben !
pi@raspberrypi:~ $ sudo apt install redis Reading package lists... Done Building dependency tree... Done Reading state information... Done The following additional packages will be installed: libjemalloc2 liblua5.1-0 liblzf1 lua-bitop lua-cjson redis-server redis-tools Suggested packages: ruby-redis The following NEW packages will be installed: libjemalloc2 liblua5.1-0 liblzf1 lua-bitop lua-cjson redis redis-server redis-tools 0 upgraded, 8 newly installed, 0 to remove and 33 not upgraded. Need to get 1,159 kB of archives. After this operation, 5,239 kB of additional disk space will be used. Do you want to continue? [Y/n] y Get:1 http://deb.debian.org/debian bullseye/main arm64 libjemalloc2 arm64 5.2.1-3 [192 kB] Get:2 http://deb.debian.org/debian bullseye/main arm64 liblua5.1-0 arm64 5.1.5-8.1+b3 [99.5 kB] Get:3 http://deb.debian.org/debian bullseye/main arm64 liblzf1 arm64 3.6-3 [9,860 B] Get:4 http://deb.debian.org/debian bullseye/main arm64 lua-bitop arm64 1.0.2-5 [6,508 B] Get:5 http://deb.debian.org/debian bullseye/main arm64 lua-cjson arm64 2.1.0+dfsg-2.1 [16.1 kB] Get:6 http://deb.debian.org/debian bullseye/main arm64 redis-tools arm64 5:6.0.16-1+deb11u2 [680 kB] Get:7 http://deb.debian.org/debian bullseye/main arm64 redis-server arm64 5:6.0.16-1+deb11u2 [98.2 kB] Get:8 http://deb.debian.org/debian bullseye/main arm64 redis all 5:6.0.16-1+deb11u2 [56.8 kB] Fetched 1,159 kB in 0s (2,482 kB/s) Selecting previously unselected package libjemalloc2:arm64. (Reading database ... 47621 files and directories currently installed.) Preparing to unpack .../0-libjemalloc2_5.2.1-3_arm64.deb ... Unpacking libjemalloc2:arm64 (5.2.1-3) ... Selecting previously unselected package liblua5.1-0:arm64. Preparing to unpack .../1-liblua5.1-0_5.1.5-8.1+b3_arm64.deb ... Unpacking liblua5.1-0:arm64 (5.1.5-8.1+b3) ... Selecting previously unselected package liblzf1:arm64. Preparing to unpack .../2-liblzf1_3.6-3_arm64.deb ... Unpacking liblzf1:arm64 (3.6-3) ... Selecting previously unselected package lua-bitop:arm64. Preparing to unpack .../3-lua-bitop_1.0.2-5_arm64.deb ... Unpacking lua-bitop:arm64 (1.0.2-5) ... Selecting previously unselected package lua-cjson:arm64. Preparing to unpack .../4-lua-cjson_2.1.0+dfsg-2.1_arm64.deb ... Unpacking lua-cjson:arm64 (2.1.0+dfsg-2.1) ... Selecting previously unselected package redis-tools. Preparing to unpack .../5-redis-tools_5%3a6.0.16-1+deb11u2_arm64.deb ... Unpacking redis-tools (5:6.0.16-1+deb11u2) ... Selecting previously unselected package redis-server. Preparing to unpack .../6-redis-server_5%3a6.0.16-1+deb11u2_arm64.deb ... Unpacking redis-server (5:6.0.16-1+deb11u2) ... Selecting previously unselected package redis. Preparing to unpack .../7-redis_5%3a6.0.16-1+deb11u2_all.deb ... Unpacking redis (5:6.0.16-1+deb11u2) ... Setting up libjemalloc2:arm64 (5.2.1-3) ... Setting up lua-cjson:arm64 (2.1.0+dfsg-2.1) ... Setting up liblzf1:arm64 (3.6-3) ... Setting up lua-bitop:arm64 (1.0.2-5) ... Setting up liblua5.1-0:arm64 (5.1.5-8.1+b3) ... Setting up redis-tools (5:6.0.16-1+deb11u2) ... Setting up redis-server (5:6.0.16-1+deb11u2) ... Created symlink /etc/systemd/system/redis.service → /lib/systemd/system/redis-server.service. Created symlink /etc/systemd/system/multi-user.target.wants/redis-server.service → /lib/systemd/system/redis-server.service. Setting up redis (5:6.0.16-1+deb11u2) ... Processing triggers for man-db (2.9.4-2) ... Processing triggers for libc-bin (2.31-13+rpt2+rpi1+deb11u4) ... pi@raspberrypi:~ $ apt policy redis redis: Installed: 5:6.0.16-1+deb11u2 Candidate: 5:6.0.16-1+deb11u2 Version table: *** 5:6.0.16-1+deb11u2 500 500 http://deb.debian.org/debian bullseye/main arm64 Packages 500 http://deb.debian.org/debian bullseye/main armhf Packages 500 http://security.debian.org/debian-security bullseye-security/main arm64 Packages 500 http://security.debian.org/debian-security bullseye-security/main armhf Packages 100 /var/lib/dpkg/status pi@raspberrypi:~ $ iobroker list instances + system.adapter.admin.0 : admin : raspberrypi - enabled, port: 8081, bind: 0.0.0.0, ru n as: admin system.adapter.backitup.0 : backitup : raspberrypi - enabled system.adapter.cloud.0 : cloud : raspberrypi - disabled system.adapter.discovery.0 : discovery : raspberrypi - disabled system.adapter.flot.0 : flot : raspberrypi - disabled system.adapter.history.0 : history : raspberrypi - disabled system.adapter.hs100.0 : hs100 : raspberrypi - disabled system.adapter.hue.0 : hue : raspberrypi - disabled, port: 443 system.adapter.info.0 : info : raspberrypi - disabled system.adapter.iot.0 : iot : raspberrypi - disabled system.adapter.javascript.0 : javascript : raspberrypi - disabled system.adapter.js2fs.0 : js2fs : raspberrypi - disabled system.adapter.mihome-vacuum.0 : mihome-vacuum : raspberrypi - disabled, port: 54321 system.adapter.mobile.0 : mobile : raspberrypi - disabled system.adapter.ping.0 : ping : raspberrypi - disabled system.adapter.pushover.0 : pushover : raspberrypi - disabled system.adapter.pushsafer.0 : pushsafer : raspberrypi - disabled system.adapter.rpi2.0 : rpi2 : raspberrypi - disabled system.adapter.samsung.0 : samsung : raspberrypi - disabled system.adapter.scenes.0 : scenes : raspberrypi - disabled system.adapter.socketio.0 : socketio : raspberrypi - disabled, port: 8084, bind: 0.0.0.0, ru n as: admin system.adapter.telegram.0 : telegram : raspberrypi - disabled, port: 8443, bind: 0.0.0.0 system.adapter.text2command.0 : text2command : raspberrypi - disabled system.adapter.upnp.0 : upnp : raspberrypi - disabled system.adapter.vis-hqwidgets.0 : vis-hqwidgets : raspberrypi - disabled system.adapter.vis.0 : vis : raspberrypi - disabled system.adapter.web.0 : web : raspberrypi - disabled, port: 8082, bind: 0.0.0.0, ru n as: admin + instance is alive -
Nach der Installation von redis konnte ich jetzt wenigstens meine Adapter alle wieder sehen.
Irgendwas vom Backup ist also da, nur sind die meisten Adapter disabled.
I konnte die jetzt nacheinander wieder aktivieren, nur dauerte das bei manchen etwas und auch mehrere Versuche...Scheint nun aber alles geklappt zu haben !
pi@raspberrypi:~ $ sudo apt install redis Reading package lists... Done Building dependency tree... Done Reading state information... Done The following additional packages will be installed: libjemalloc2 liblua5.1-0 liblzf1 lua-bitop lua-cjson redis-server redis-tools Suggested packages: ruby-redis The following NEW packages will be installed: libjemalloc2 liblua5.1-0 liblzf1 lua-bitop lua-cjson redis redis-server redis-tools 0 upgraded, 8 newly installed, 0 to remove and 33 not upgraded. Need to get 1,159 kB of archives. After this operation, 5,239 kB of additional disk space will be used. Do you want to continue? [Y/n] y Get:1 http://deb.debian.org/debian bullseye/main arm64 libjemalloc2 arm64 5.2.1-3 [192 kB] Get:2 http://deb.debian.org/debian bullseye/main arm64 liblua5.1-0 arm64 5.1.5-8.1+b3 [99.5 kB] Get:3 http://deb.debian.org/debian bullseye/main arm64 liblzf1 arm64 3.6-3 [9,860 B] Get:4 http://deb.debian.org/debian bullseye/main arm64 lua-bitop arm64 1.0.2-5 [6,508 B] Get:5 http://deb.debian.org/debian bullseye/main arm64 lua-cjson arm64 2.1.0+dfsg-2.1 [16.1 kB] Get:6 http://deb.debian.org/debian bullseye/main arm64 redis-tools arm64 5:6.0.16-1+deb11u2 [680 kB] Get:7 http://deb.debian.org/debian bullseye/main arm64 redis-server arm64 5:6.0.16-1+deb11u2 [98.2 kB] Get:8 http://deb.debian.org/debian bullseye/main arm64 redis all 5:6.0.16-1+deb11u2 [56.8 kB] Fetched 1,159 kB in 0s (2,482 kB/s) Selecting previously unselected package libjemalloc2:arm64. (Reading database ... 47621 files and directories currently installed.) Preparing to unpack .../0-libjemalloc2_5.2.1-3_arm64.deb ... Unpacking libjemalloc2:arm64 (5.2.1-3) ... Selecting previously unselected package liblua5.1-0:arm64. Preparing to unpack .../1-liblua5.1-0_5.1.5-8.1+b3_arm64.deb ... Unpacking liblua5.1-0:arm64 (5.1.5-8.1+b3) ... Selecting previously unselected package liblzf1:arm64. Preparing to unpack .../2-liblzf1_3.6-3_arm64.deb ... Unpacking liblzf1:arm64 (3.6-3) ... Selecting previously unselected package lua-bitop:arm64. Preparing to unpack .../3-lua-bitop_1.0.2-5_arm64.deb ... Unpacking lua-bitop:arm64 (1.0.2-5) ... Selecting previously unselected package lua-cjson:arm64. Preparing to unpack .../4-lua-cjson_2.1.0+dfsg-2.1_arm64.deb ... Unpacking lua-cjson:arm64 (2.1.0+dfsg-2.1) ... Selecting previously unselected package redis-tools. Preparing to unpack .../5-redis-tools_5%3a6.0.16-1+deb11u2_arm64.deb ... Unpacking redis-tools (5:6.0.16-1+deb11u2) ... Selecting previously unselected package redis-server. Preparing to unpack .../6-redis-server_5%3a6.0.16-1+deb11u2_arm64.deb ... Unpacking redis-server (5:6.0.16-1+deb11u2) ... Selecting previously unselected package redis. Preparing to unpack .../7-redis_5%3a6.0.16-1+deb11u2_all.deb ... Unpacking redis (5:6.0.16-1+deb11u2) ... Setting up libjemalloc2:arm64 (5.2.1-3) ... Setting up lua-cjson:arm64 (2.1.0+dfsg-2.1) ... Setting up liblzf1:arm64 (3.6-3) ... Setting up lua-bitop:arm64 (1.0.2-5) ... Setting up liblua5.1-0:arm64 (5.1.5-8.1+b3) ... Setting up redis-tools (5:6.0.16-1+deb11u2) ... Setting up redis-server (5:6.0.16-1+deb11u2) ... Created symlink /etc/systemd/system/redis.service → /lib/systemd/system/redis-server.service. Created symlink /etc/systemd/system/multi-user.target.wants/redis-server.service → /lib/systemd/system/redis-server.service. Setting up redis (5:6.0.16-1+deb11u2) ... Processing triggers for man-db (2.9.4-2) ... Processing triggers for libc-bin (2.31-13+rpt2+rpi1+deb11u4) ... pi@raspberrypi:~ $ apt policy redis redis: Installed: 5:6.0.16-1+deb11u2 Candidate: 5:6.0.16-1+deb11u2 Version table: *** 5:6.0.16-1+deb11u2 500 500 http://deb.debian.org/debian bullseye/main arm64 Packages 500 http://deb.debian.org/debian bullseye/main armhf Packages 500 http://security.debian.org/debian-security bullseye-security/main arm64 Packages 500 http://security.debian.org/debian-security bullseye-security/main armhf Packages 100 /var/lib/dpkg/status pi@raspberrypi:~ $ iobroker list instances + system.adapter.admin.0 : admin : raspberrypi - enabled, port: 8081, bind: 0.0.0.0, ru n as: admin system.adapter.backitup.0 : backitup : raspberrypi - enabled system.adapter.cloud.0 : cloud : raspberrypi - disabled system.adapter.discovery.0 : discovery : raspberrypi - disabled system.adapter.flot.0 : flot : raspberrypi - disabled system.adapter.history.0 : history : raspberrypi - disabled system.adapter.hs100.0 : hs100 : raspberrypi - disabled system.adapter.hue.0 : hue : raspberrypi - disabled, port: 443 system.adapter.info.0 : info : raspberrypi - disabled system.adapter.iot.0 : iot : raspberrypi - disabled system.adapter.javascript.0 : javascript : raspberrypi - disabled system.adapter.js2fs.0 : js2fs : raspberrypi - disabled system.adapter.mihome-vacuum.0 : mihome-vacuum : raspberrypi - disabled, port: 54321 system.adapter.mobile.0 : mobile : raspberrypi - disabled system.adapter.ping.0 : ping : raspberrypi - disabled system.adapter.pushover.0 : pushover : raspberrypi - disabled system.adapter.pushsafer.0 : pushsafer : raspberrypi - disabled system.adapter.rpi2.0 : rpi2 : raspberrypi - disabled system.adapter.samsung.0 : samsung : raspberrypi - disabled system.adapter.scenes.0 : scenes : raspberrypi - disabled system.adapter.socketio.0 : socketio : raspberrypi - disabled, port: 8084, bind: 0.0.0.0, ru n as: admin system.adapter.telegram.0 : telegram : raspberrypi - disabled, port: 8443, bind: 0.0.0.0 system.adapter.text2command.0 : text2command : raspberrypi - disabled system.adapter.upnp.0 : upnp : raspberrypi - disabled system.adapter.vis-hqwidgets.0 : vis-hqwidgets : raspberrypi - disabled system.adapter.vis.0 : vis : raspberrypi - disabled system.adapter.web.0 : web : raspberrypi - disabled, port: 8082, bind: 0.0.0.0, ru n as: admin + instance is alive -
pi@raspberrypi:~ $ sudo apt update Hit:1 http://deb.debian.org/debian bullseye InRelease Get:2 http://deb.debian.org/debian bullseye-updates InRelease [44.1 kB] Get:3 http://archive.raspberrypi.org/debian bullseye InRelease [23.6 kB] Get:4 http://security.debian.org/debian-security bullseye-security InRelease [48 .4 kB] Hit:5 https://deb.nodesource.com/node_16.x bullseye InRelease Get:6 http://archive.raspberrypi.org/debian bullseye/main armhf Packages [308 kB ] Get:7 http://archive.raspberrypi.org/debian bullseye/main arm64 Packages [299 kB ] Fetched 723 kB in 3s (274 kB/s) Reading package lists... Done Building dependency tree... Done Reading state information... Done 33 packages can be upgraded. Run 'apt list --upgradable' to see them. pi@raspberrypi:~ $ apt list --upgradable Listing... Done bind9-host/stable-security 1:9.16.33-1~deb11u1 arm64 [upgradable from: 1:9.16.27-1~deb11u1] bind9-libs/stable-security 1:9.16.33-1~deb11u1 arm64 [upgradable from: 1:9.16.27-1~deb11u1] bluez-firmware/stable,stable 1.2-4+rpt9 all [upgradable from: 1.2-4+rpt8] bluez/stable 5.55-3.1+rpt2 arm64 [upgradable from: 5.55-3.1+rpt1] dhcpcd5/stable 1:8.1.2-1+rpt9 arm64 [upgradable from: 1:8.1.2-1+rpt7] isc-dhcp-client/stable-security 4.4.1-2.3+deb11u1 arm64 [upgradable from: 4.4.1-2.3] isc-dhcp-common/stable-security 4.4.1-2.3+deb11u1 arm64 [upgradable from: 4.4.1-2.3] libbluetooth3/stable 5.55-3.1+rpt2 arm64 [upgradable from: 5.55-3.1+rpt1] libc-bin/stable 2.31-13+rpt2+rpi1+deb11u5 arm64 [upgradable from: 2.31-13+rpt2+rpi1+deb11u4] libc-dev-bin/stable 2.31-13+rpt2+rpi1+deb11u5 arm64 [upgradable from: 2.31-13+rpt2+rpi1+deb11u4] libc-devtools/stable 2.31-13+rpt2+rpi1+deb11u5 arm64 [upgradable from: 2.31-13+rpt2+rpi1+deb11u4] libc-l10n/stable,stable 2.31-13+rpt2+rpi1+deb11u5 all [upgradable from: 2.31-13+rpt2+rpi1+deb11u4] libc6-dbg/stable 2.31-13+rpt2+rpi1+deb11u5 arm64 [upgradable from: 2.31-13+rpt2+rpi1+deb11u4] libc6-dev/stable 2.31-13+rpt2+rpi1+deb11u5 arm64 [upgradable from: 2.31-13+rpt2+rpi1+deb11u4] libc6/stable 2.31-13+rpt2+rpi1+deb11u5 arm64 [upgradable from: 2.31-13+rpt2+rpi1+deb11u4] libcamera-apps-lite/stable 0~git20221109+73ab09f-1 arm64 [upgradable from: 0~git20220830+1bf0cca-1] libcamera0/stable 0~git20221109+d528119f-1 arm64 [upgradable from: 0~git20220826+3fad116f-1] libkms++0/stable 0~git20221104~171243+adc05b6-1 arm64 [upgradable from: 0~git20211110~105525+2236a8c-1] libksba8/stable-security 1.5.0-3+deb11u1 arm64 [upgradable from: 1.5.0-3] libntfs-3g883/stable-security 1:2017.3.23AR.3-4+deb11u3 arm64 [upgradable from: 1:2017.3.23AR.3-4+deb11u2] libxml2/stable-security 2.9.10+dfsg-6.7+deb11u3 arm64 [upgradable from: 2.9.10+dfsg-6.7+deb11u2] linux-libc-dev/stable 1:1.20221104-1 arm64 [upgradable from: 1:1.20220830-1] locales/stable,stable 2.31-13+rpt2+rpi1+deb11u5 all [upgradable from: 2.31-13+rpt2+rpi1+deb11u4] ntfs-3g/stable-security 1:2017.3.23AR.3-4+deb11u3 arm64 [upgradable from: 1:2017.3.23AR.3-4+deb11u2] python3-kms++/stable 0~git20221104~171243+adc05b6-1 arm64 [upgradable from: 0~git20211110~105525+2236a8c-1] python3-libcamera/stable 0~git20221109+d528119f-1 arm64 [upgradable from: 0~git20220826+3fad116f-1] python3-picamera2/stable,stable 0.3.6-1 all [upgradable from: 0.3.3-1] raspberrypi-bootloader/stable 1:1.20221104-1 arm64 [upgradable from: 1:1.20220830-1] raspberrypi-kernel/stable 1:1.20221104-1 arm64 [upgradable from: 1:1.20220830-1] raspberrypi-sys-mods/stable 20221019 arm64 [upgradable from: 20220915] raspi-config/stable,stable 20221018 all [upgradable from: 20220920] rpi-eeprom/stable 13.21-1 arm64 [upgradable from: 13.16-1] tzdata/stable-updates,stable-updates 2021a-1+deb11u8 all [upgradable from: 2021a-1+deb11u5]


