NEWS
PH-Messung
-
Hi, maybe it would be easier to make a backup of the firmware from the ESP and then just change the gateway and play back again. Something like that works with Esptool.py , but I don't know my way around that well either.
-
Hey,
I hope I also get my device in next 1 days (just ordered yesterday). When the code I found telling anything AND when it is right that the App also switches to "local" communication when in same WLAN then honestly I would start really analyzing that. That could be way more easy!
Code wise it seemed to me that locally the device itself acts as a simple mqtt server hopefully.So if someone wants to do stuff in between:
- maybe start with a nmap scan against the local IP ... is there anything open and what can be found there?
- start (like @coyote started) with Wireshark but focus on mobile device/App-with-ph-803w communication ... there should be some
Anyone up for that?
PS: @Marc-R
Hi yall, my first post so be gentle...
We are always :-)
To maybe see more in the data would be a good idea to also see what data the device was showing as you tried it, maybe the "calculation rules" that @Anti was able to decode also apply. ALso interesting would be which part o fthe message is changing when the values change and which part stays static. So now you need to start "data crunching", I expect the data needs to be in there
-
Hey,
I hope I also get my device in next 1 days (just ordered yesterday). When the code I found telling anything AND when it is right that the App also switches to "local" communication when in same WLAN then honestly I would start really analyzing that. That could be way more easy!
Code wise it seemed to me that locally the device itself acts as a simple mqtt server hopefully.So if someone wants to do stuff in between:
- maybe start with a nmap scan against the local IP ... is there anything open and what can be found there?
- start (like @coyote started) with Wireshark but focus on mobile device/App-with-ph-803w communication ... there should be some
Anyone up for that?
PS: @Marc-R
Hi yall, my first post so be gentle...
We are always :-)
To maybe see more in the data would be a good idea to also see what data the device was showing as you tried it, maybe the "calculation rules" that @Anti was able to decode also apply. ALso interesting would be which part o fthe message is changing when the values change and which part stays static. So now you need to start "data crunching", I expect the data needs to be in there
Today I made a local scan in the same network. At the first attempt it was over the VPN connection and therefore "Remote"
Maybe you like that better @apollon77 ;-)
39484 33.259423 192.168.66.54 192.168.66.8 TCP 62 12416 → 48158 [PSH, ACK] Seq=94 Ack=83 Win=5758 Len=8 29590 29.524847 192.168.66.54 192.168.66.8 TCP 62 12416 → 48158 [PSH, ACK] Seq=86 Ack=75 Win=5766 Len=8 26127 28.341450 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 18180 25.193896 192.168.66.54 192.168.66.8 TCP 62 12416 → 48158 [PSH, ACK] Seq=78 Ack=67 Win=5774 Len=8 8826 21.298249 192.168.66.54 192.168.66.8 TCP 62 12416 → 48158 [PSH, ACK] Seq=70 Ack=59 Win=5782 Len=8 8700 21.257654 192.168.66.54 192.168.66.8 TCP 76 12416 → 48158 [PSH, ACK] Seq=48 Ack=51 Win=5790 Len=22 8696 21.255005 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 7288 20.836871 192.168.66.54 192.168.66.8 TCP 72 12416 → 48158 [PSH, ACK] Seq=30 Ack=38 Win=5803 Len=18 7287 20.824022 192.168.66.54 192.168.66.8 TCP 54 12416 → 48158 [ACK] Seq=30 Ack=38 Win=5803 Len=0 6978 20.574620 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 5694 20.118304 192.168.66.54 192.168.66.8 TCP 63 12416 → 48158 [PSH, ACK] Seq=21 Ack=29 Win=5812 Len=9 5643 20.100519 192.168.66.54 192.168.66.8 TCP 74 12416 → 48158 [PSH, ACK] Seq=1 Ack=9 Win=5832 Len=20 5607 20.088883 192.168.66.54 192.168.66.8 TCP 58 12416 → 48158 [SYN, ACK] Seq=0 Ack=1 Win=5840 Len=0 MSS=1460 3855 19.504039 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 2761 18.290828 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 2567 17.284353 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 2381 16.220137 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 2210 15.190409 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 2063 14.544840 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 1906 13.514199 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 1662 12.248355 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 -
Today I made a local scan in the same network. At the first attempt it was over the VPN connection and therefore "Remote"
Maybe you like that better @apollon77 ;-)
39484 33.259423 192.168.66.54 192.168.66.8 TCP 62 12416 → 48158 [PSH, ACK] Seq=94 Ack=83 Win=5758 Len=8 29590 29.524847 192.168.66.54 192.168.66.8 TCP 62 12416 → 48158 [PSH, ACK] Seq=86 Ack=75 Win=5766 Len=8 26127 28.341450 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 18180 25.193896 192.168.66.54 192.168.66.8 TCP 62 12416 → 48158 [PSH, ACK] Seq=78 Ack=67 Win=5774 Len=8 8826 21.298249 192.168.66.54 192.168.66.8 TCP 62 12416 → 48158 [PSH, ACK] Seq=70 Ack=59 Win=5782 Len=8 8700 21.257654 192.168.66.54 192.168.66.8 TCP 76 12416 → 48158 [PSH, ACK] Seq=48 Ack=51 Win=5790 Len=22 8696 21.255005 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 7288 20.836871 192.168.66.54 192.168.66.8 TCP 72 12416 → 48158 [PSH, ACK] Seq=30 Ack=38 Win=5803 Len=18 7287 20.824022 192.168.66.54 192.168.66.8 TCP 54 12416 → 48158 [ACK] Seq=30 Ack=38 Win=5803 Len=0 6978 20.574620 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 5694 20.118304 192.168.66.54 192.168.66.8 TCP 63 12416 → 48158 [PSH, ACK] Seq=21 Ack=29 Win=5812 Len=9 5643 20.100519 192.168.66.54 192.168.66.8 TCP 74 12416 → 48158 [PSH, ACK] Seq=1 Ack=9 Win=5832 Len=20 5607 20.088883 192.168.66.54 192.168.66.8 TCP 58 12416 → 48158 [SYN, ACK] Seq=0 Ack=1 Win=5840 Len=0 MSS=1460 3855 19.504039 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 2761 18.290828 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 2567 17.284353 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 2381 16.220137 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 2210 15.190409 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 2063 14.544840 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 1906 13.514199 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 1662 12.248355 192.168.66.54 192.168.66.8 UDP 151 12414 → 37038 Len=109 -
@coyote yes. Via VPN normally all UDP messages are not transferred ;-)
Can you send me that wireshark file via email to iobroker@fischer-ka.de
Ps: i assume .54 is the ph803 and the .8 is mobile device?
@apollon77 ok, i didn't know.
Sure, think it'll take another hour, then I can send it to you.
Yes exactly. .54 is the 803W and .8 is the smartphone
-
@coyote yes. Via VPN normally all UDP messages are not transferred ;-)
Can you send me that wireshark file via email to iobroker@fischer-ka.de
Ps: i assume .54 is the ph803 and the .8 is mobile device?
@apollon77 you have mail ;-)
-
Das mal zur App vieleicht kann jemand was damit anfangen.
https://docs.gizwits.com/en-us/AppDev/AndroidSDKA2.html#5-Device-control
Dafür ist mein Englich zu schlecht. Wenn ich das richtig verstehe kann und darf man an der App was ändern mit
Android Studio -
@apollon77 you have mail ;-)
@coyote Ok, I start to collect here the stuff I saw in the Wireshark:
-
(01) App sends a UDP broadcast with data "00 00 00 03 03 00 00 03" to port 12414
-
App sends MDNS query to 224.0.0.251 _%9E5E7C8F47989526C9BCD95D24084F6F0B27C5ED._sub._googlecast._tcp.local, "QU" question PTR _googlecast._tcp.local, "QU" question
-
(02) Device Answers with UDP message from port 12414 to App
00:00:00:03:68:00:00:04:00:16:43:46:71:70:4a:54:53:79:6d:43:45:39:50:4c:6c:70:31:44:70:62:68:59:00:06:48:3f:da:87:dc:47:00:00:00:20:32:64:33:64:39:35:34:64:39:62:62:37:34:31:62:34:61:31:39:62:61:31:31:35:33:31:30:34:39:33:32:62:00:00:00:00:00:00:00:02:61:70:69:2e:67:69:7a:77:69:74:73:2e:63:6f:6d:3a:38:30:00:34:2e:30:2e:38:00
( hCFqpJTSymCE9PLlp1DpbhYH?ÚÜG 2d3d954d9bb741b4a19ba1153104932bapi.gizwits.com:804.0.8) -
App connects to device on port 12416 and Device and App communicates on that port
-
(03) App sends 00:00:00:03:03:00:00:06
-
(04) Device answers: 00:00:00:03:0f:00:00:07:00:0a:X1:X2:X3:X4:X5:X6:X7:X8:X9:X0
-
(05) App sends : 00:00:00:03:0f:00:00:08:00:0a:X1:X2:X3:X4:X5:X6:X7:X8:X9:X0
-
(06) Device answers: 00:00:00:03:04:00:00:09:00
-
(07) App sends : 00:00:00:03:04:00:00:90:02
-
(08) Device answers: 00:00:00:03:0d:00:00:91:03:00:02:dc:08:9d:00:00:00:00
-
(09) App sends : 00:00:00:03:08:00:00:93:00:00:00:04:02
-
(10) Device answers: 00:00:00:03:11:00:00:94:00:00:00:04:03:00:02:dc:08:9d:00:00:00:00
-
(11) App sends : 00:00:00:03:03:00:00:15
-
(12) Device answers: 00:00:00:03:03:00:00:16
... and the last two repeat every 4s (seems like a ping/pong)
Das passt grob spontan zu dem Protokoll von hier https://github.com/gizwits/gokit-GAgent/blob/master/software/lan/lan.c#L291
- 00 00 00 03 sind immer die lokalen ersten Bytes
- byte Nummer 8 ist das "Kommando" (also wenn App->Device) ... damit von oben
- (---) code 01 -- UDP to device - onBoarding message ... 00 XX <XX bytes ssid> 00 YY <YY bytes ssidpwd> (unsure with 00xx/yy or if only xx/yy?)
- (---) code 02 -- UDP from device - onBoarding response ... just as OK message
- (01): code 03 -- UDP to device - Discover message
- (02): code 04 ?? -- UDP from device - Discover response
- (---) code 05 ?? -- UDP from device active broadcast from device
- (03): code 06 -- TCP to device: user bind passcode; Device returns passcode for login command
- (04): code 07 -- TCP from device: device answers with data and 10 chars as passcode
- (05): code 08 -- TCP to device: user login : Device wants to see the same passcode as sent above
- (06): code 09 -- TCP from device: login result: 00=ok, 01=error
- (07): code 90 -- TCP to device: send p0 to uart ... schreibt "02" ans Device
- (08): code 91 ?? TCP answer from serial?? 03:00 02:dc 08:9d 00:00 00:00
- (09): code 93 ?? -- TCP to device - unknown 00:00:00:04:02
- (10): code 94 ?? -- TCP from device - unknown 00:00 00:04 03:00 02:dc 08:9d 00:00 00:00
- (11) code 15: -- TCP to device: "tick" aka ping
- (12) code 16: should be "pong" then
If we now would have info on the values on display vs data it would help :-)
- 02dc could be 732 with idea from above with /100 == 7,32 ... PH??
- 089d could be 2205 with idea from above -2000 === 205 ... ORP?
@coyote ??
The two other 00 00 at the end could be the switch states ... but also would need to be verified.
Ingo
-
-
@coyote Ok, I start to collect here the stuff I saw in the Wireshark:
-
(01) App sends a UDP broadcast with data "00 00 00 03 03 00 00 03" to port 12414
-
App sends MDNS query to 224.0.0.251 _%9E5E7C8F47989526C9BCD95D24084F6F0B27C5ED._sub._googlecast._tcp.local, "QU" question PTR _googlecast._tcp.local, "QU" question
-
(02) Device Answers with UDP message from port 12414 to App
00:00:00:03:68:00:00:04:00:16:43:46:71:70:4a:54:53:79:6d:43:45:39:50:4c:6c:70:31:44:70:62:68:59:00:06:48:3f:da:87:dc:47:00:00:00:20:32:64:33:64:39:35:34:64:39:62:62:37:34:31:62:34:61:31:39:62:61:31:31:35:33:31:30:34:39:33:32:62:00:00:00:00:00:00:00:02:61:70:69:2e:67:69:7a:77:69:74:73:2e:63:6f:6d:3a:38:30:00:34:2e:30:2e:38:00
( hCFqpJTSymCE9PLlp1DpbhYH?ÚÜG 2d3d954d9bb741b4a19ba1153104932bapi.gizwits.com:804.0.8) -
App connects to device on port 12416 and Device and App communicates on that port
-
(03) App sends 00:00:00:03:03:00:00:06
-
(04) Device answers: 00:00:00:03:0f:00:00:07:00:0a:X1:X2:X3:X4:X5:X6:X7:X8:X9:X0
-
(05) App sends : 00:00:00:03:0f:00:00:08:00:0a:X1:X2:X3:X4:X5:X6:X7:X8:X9:X0
-
(06) Device answers: 00:00:00:03:04:00:00:09:00
-
(07) App sends : 00:00:00:03:04:00:00:90:02
-
(08) Device answers: 00:00:00:03:0d:00:00:91:03:00:02:dc:08:9d:00:00:00:00
-
(09) App sends : 00:00:00:03:08:00:00:93:00:00:00:04:02
-
(10) Device answers: 00:00:00:03:11:00:00:94:00:00:00:04:03:00:02:dc:08:9d:00:00:00:00
-
(11) App sends : 00:00:00:03:03:00:00:15
-
(12) Device answers: 00:00:00:03:03:00:00:16
... and the last two repeat every 4s (seems like a ping/pong)
Das passt grob spontan zu dem Protokoll von hier https://github.com/gizwits/gokit-GAgent/blob/master/software/lan/lan.c#L291
- 00 00 00 03 sind immer die lokalen ersten Bytes
- byte Nummer 8 ist das "Kommando" (also wenn App->Device) ... damit von oben
- (---) code 01 -- UDP to device - onBoarding message ... 00 XX <XX bytes ssid> 00 YY <YY bytes ssidpwd> (unsure with 00xx/yy or if only xx/yy?)
- (---) code 02 -- UDP from device - onBoarding response ... just as OK message
- (01): code 03 -- UDP to device - Discover message
- (02): code 04 ?? -- UDP from device - Discover response
- (---) code 05 ?? -- UDP from device active broadcast from device
- (03): code 06 -- TCP to device: user bind passcode; Device returns passcode for login command
- (04): code 07 -- TCP from device: device answers with data and 10 chars as passcode
- (05): code 08 -- TCP to device: user login : Device wants to see the same passcode as sent above
- (06): code 09 -- TCP from device: login result: 00=ok, 01=error
- (07): code 90 -- TCP to device: send p0 to uart ... schreibt "02" ans Device
- (08): code 91 ?? TCP answer from serial?? 03:00 02:dc 08:9d 00:00 00:00
- (09): code 93 ?? -- TCP to device - unknown 00:00:00:04:02
- (10): code 94 ?? -- TCP from device - unknown 00:00 00:04 03:00 02:dc 08:9d 00:00 00:00
- (11) code 15: -- TCP to device: "tick" aka ping
- (12) code 16: should be "pong" then
If we now would have info on the values on display vs data it would help :-)
- 02dc could be 732 with idea from above with /100 == 7,32 ... PH??
- 089d could be 2205 with idea from above -2000 === 205 ... ORP?
@coyote ??
The two other 00 00 at the end could be the switch states ... but also would need to be verified.
Ingo
@apollon77 sounds good ;-)
Will do more test today with wireshark and and will write down the values from the display or take pictures.
The switches cannot be triggered manually.
The device is currently not in use by me, there are no probes connected, so the values are not directly plausible (ORP 0.2 etc.) -
-
Hi yall, my first post so be gentle...
I connected the TX/RX inside the PH-803W with my UART to see what is shown there:
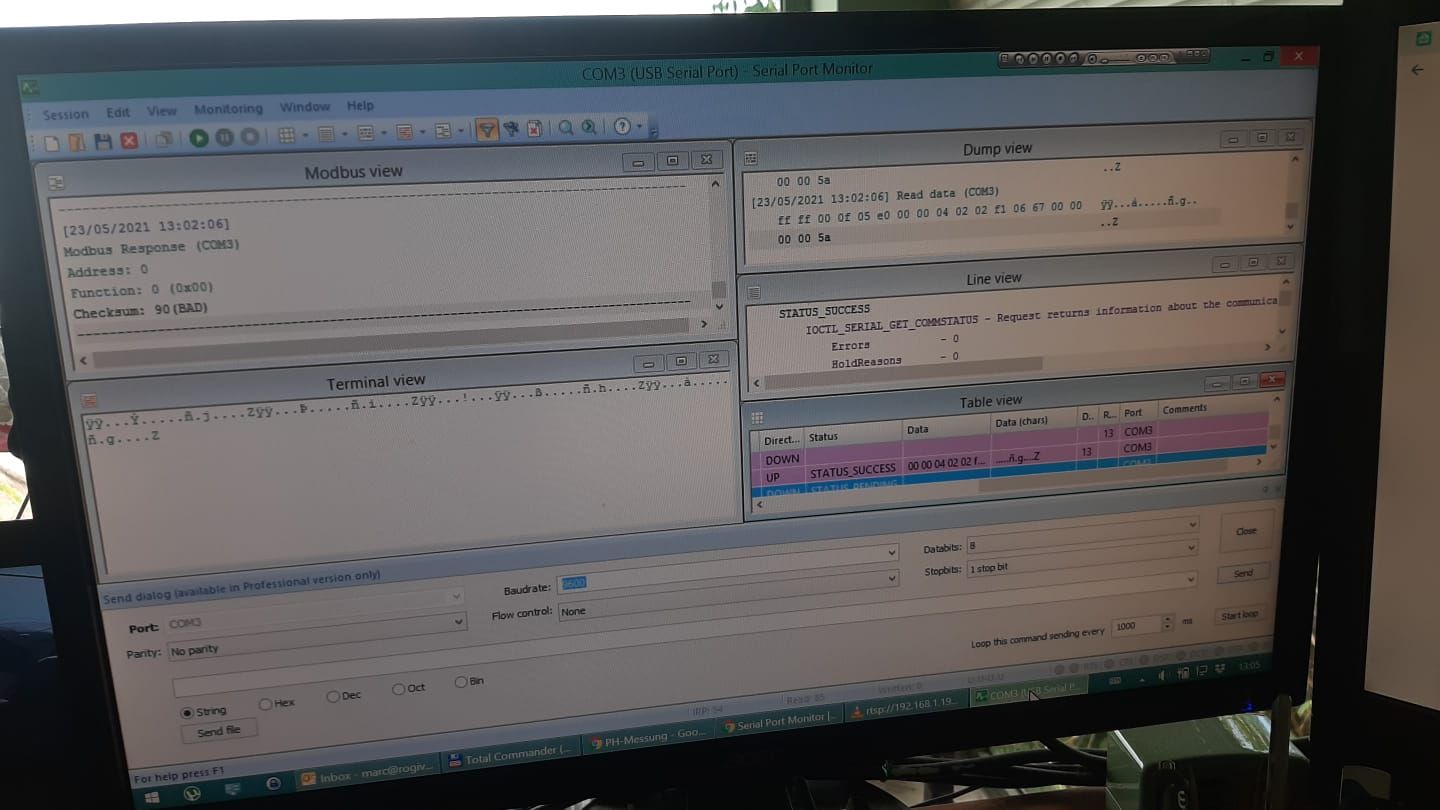
Seems it sends the same binary data that Anti was able to reroute to his MQTT? While my router has the NAT functionality, I unfortunately cannot define virtual IP addresses, so that route is not viable for me and probably most here. But if we can make sense of the TX/RX Data, we could potentially add another ESP on this port and let it send the data to where we want it to be sent?
Hope this makes sense and is helpful for the discussuion, Cheers
@marc-r Thats nice Marc-r. So the ESP just bring the Serial kommunikation to the Network. What I allready suspected but didn't checked. I think, like you, is the most simple way to flash the original ESP (or put a second one if you want to keep the original).
for the completness: 9600 8N1
I think I will make that, to don't have the MQTT in the middle.
-
@marc-r Thats nice Marc-r. So the ESP just bring the Serial kommunikation to the Network. What I allready suspected but didn't checked. I think, like you, is the most simple way to flash the original ESP (or put a second one if you want to keep the original).
for the completness: 9600 8N1
I think I will make that, to don't have the MQTT in the middle.
@anti Why you dio not implement the LAN protocol? (or wait until I did?) For me personally hardware modifications are meeh ... but I think everyone has it's own opinion here :-)
But in gfact does not hatter ... so we need to dectode the values ... we know 4 bytes already :-) So assumption stay that the 2x 0000 at the end are the states of the switches
-
@marc-r Thats nice Marc-r. So the ESP just bring the Serial kommunikation to the Network. What I allready suspected but didn't checked. I think, like you, is the most simple way to flash the original ESP (or put a second one if you want to keep the original).
for the completness: 9600 8N1
I think I will make that, to don't have the MQTT in the middle.
-
@anti you mean load something like Tasmota on the existing ESP? I have a lot of Sonoff switches which I "tasmotized", so I know how that works, but I'm not sure if the PH-803W would be compatible?
@marc-r I'm not so deep in the MQTT/Tasmota Topic. So not sure what you can do with Tasmota, here in this use case we want to put a serial Input somewhere. When Tasmota can do that, you should be okay with that. I was thinking about a little Programm on ESP putting the serial e.g. on a Webpage. This is probably a few minutes programming Job. I think i prefare this, because my Pool also will be controlled by an ESP. If a Server is in the middle is one more thing that can fail.
But anyway i can wait if the other guys here find the "LAN Protocol" Solution. If i can use that from another ESP, i will probably make like this.
Well i just thought i can connect the 803W serial connect directly my control ESP ... this is also a good failsafe alternative.
-
@anti Tasmota is an awesome open-source firmware for all kinds of ESP8266 devices to connect them via MQTT to automation systems such as Home Assistant and others. Have a look here: https://tasmota.github.io/docs/
I virtually loaded it on about 60 devices so far, but try are Sonoff and Shelly switches and I'm not sure how the PH-803W would handle it.
I'm just adding this as another alternative to the paths you guys are already following. I'm not saying it's better or worse. If you guys find a fairly simple way to send the PH-803W data to MQTT, I'm all for it!
-
Ok, mit weiteren Wireshark Mitschnitten von @coyote bin ich denke etwas weiter ... immer noch viele Annahmen, daber die kann man dann ja mal verifizieren. habe auch eine vermutung wo die Schaltwerte stecken (Bit flags) und würde tippen das andere Bits da drin vllt im Display für Anzeigen genutzt werden ...
Ich habe mal alles unter https://github.com/Apollon77/node-ph803w/blob/main/PROTOCOL.md zusammengefasst.
Als nächstes schaue ich mal das ich das als node.js Library implementiereIch habe auch für "unsere ESP Freunde" mal eine vermutete minimale Kommunikation unter https://github.com/Apollon77/node-ph803w/blob/main/PROTOCOL.md#minimum-interaction-scheme aufgeschrieben ... wäre zu verifizieren ...
Have fun
-
Ok, mit weiteren Wireshark Mitschnitten von @coyote bin ich denke etwas weiter ... immer noch viele Annahmen, daber die kann man dann ja mal verifizieren. habe auch eine vermutung wo die Schaltwerte stecken (Bit flags) und würde tippen das andere Bits da drin vllt im Display für Anzeigen genutzt werden ...
Ich habe mal alles unter https://github.com/Apollon77/node-ph803w/blob/main/PROTOCOL.md zusammengefasst.
Als nächstes schaue ich mal das ich das als node.js Library implementiereIch habe auch für "unsere ESP Freunde" mal eine vermutete minimale Kommunikation unter https://github.com/Apollon77/node-ph803w/blob/main/PROTOCOL.md#minimum-interaction-scheme aufgeschrieben ... wäre zu verifizieren ...
Have fun
@apollon77 Respekt.:+1: Aber ich versteh nur noch Bahnhof:face_with_rolling_eyes: . Mal abwarten wie es weitergeht.
Trotzdem DANKE für die Info´s und deine Mühe -
Ok, dann mal nächster Schritt ... ich hab mal was gebaut.
- Man nehme am besten einen Rechner wo nodejs drauf ist (also der von iobroker ist super)
- per SSH einloggen und in das Vezeichnis gehen
- Man lege sich ein neues Verzechnis an, am besten direkt im User-Verzeichnis (also NICHT!! in /opt/iobroker)
npm install Apollon77/node-ph803wcd node_modules/node-ph803w/examplenode data.js 111.222.333.444(mit 111.222.333.444 die IP des PH803W Geräts im lokalen Netzwerk
Dann sollte sich das Beispielskript verbinden, Passcode holen, einloggen und jede Datenänderung die es gibt sollte eine Logzeile geben mit den Werten. Eine Datenzeile muss in jedem Fall kommen - hoffentlich mehr sobald sich was ändert. Das nehme ich gern mal.
Falls irgendwas nicht geht bitte mal unter Linux mit
DEBUG=ph803w* node data.js 111.222.333.444starten, dann sollte mehr log kommen.Zu testen ist:
- Das die werte mit dem Display passen und idealerweise auch was die "Schaltzustände" angeht
- Das bei Änderungen neue Werte kommen (es ist immer noch ein bissl unklar welches Kommando das auslöst)
- Die zwei "binFlag1/2" Felder haben vermutlich eine Verbindung zu DIngen im Display (annahme). Das wäre zu prüfen und hier schreiben zu was was gehört :-)
Dann schauen wir mal wie gut blindes Programmieren so tut :-)
Ingo
-
Ok, dann mal nächster Schritt ... ich hab mal was gebaut.
- Man nehme am besten einen Rechner wo nodejs drauf ist (also der von iobroker ist super)
- per SSH einloggen und in das Vezeichnis gehen
- Man lege sich ein neues Verzechnis an, am besten direkt im User-Verzeichnis (also NICHT!! in /opt/iobroker)
npm install Apollon77/node-ph803wcd node_modules/node-ph803w/examplenode data.js 111.222.333.444(mit 111.222.333.444 die IP des PH803W Geräts im lokalen Netzwerk
Dann sollte sich das Beispielskript verbinden, Passcode holen, einloggen und jede Datenänderung die es gibt sollte eine Logzeile geben mit den Werten. Eine Datenzeile muss in jedem Fall kommen - hoffentlich mehr sobald sich was ändert. Das nehme ich gern mal.
Falls irgendwas nicht geht bitte mal unter Linux mit
DEBUG=ph803w* node data.js 111.222.333.444starten, dann sollte mehr log kommen.Zu testen ist:
- Das die werte mit dem Display passen und idealerweise auch was die "Schaltzustände" angeht
- Das bei Änderungen neue Werte kommen (es ist immer noch ein bissl unklar welches Kommando das auslöst)
- Die zwei "binFlag1/2" Felder haben vermutlich eine Verbindung zu DIngen im Display (annahme). Das wäre zu prüfen und hier schreiben zu was was gehört :-)
Dann schauen wir mal wie gut blindes Programmieren so tut :-)
Ingo
@apollon77
Coole Nummer :DEs ginge aber auch (ein wenig einfacher) mit nem Wemos D1 / NodeMCU und ner analogen PH Sonde :D... Nur so nebenbei :+1:
Wemos D1 PH-Sonde -
Wo bleibt denn da der Spaß? :-P
Nein ist natürlich auch ein weg. Hab sowas sogar hier liegen war irgendwie nie dazu gekommen das weiterzuverfolgen :/
@anti weis ich doch. War ein wenig ironisch gemeint :) Versteh schon.. Herrausforderung und so.
Hatte ich auch vor... Bin dann aber die Tage mangels Zeit umgeschwenkt. Jetzt regelt die phileo den pH wert, n shelly steuert den Chlorinator und die Pumpe ( danke an paul :D ) und n blueconnect sendet stündlich die Daten :D ... läuft!


